___________________________________________________________
Contents
___________________________________________________________
1. A Brief Explanation of Gang Stalking:
Definition
Gang stalking – also known as “organized stalking” –
is a slang term for a set of tactics used in counterintelligence
operations involving the covert surveillance and harassment of a
targeted individual. The goal of such operations – in the parlance of
counterintelligence personnel – is to “subvert” or “neutralize” an
individual deemed by a government agency (or its informants) to be an
enemy.
Strategy and Tactics
Organized
stalking methods were used extensively by communist East Germany’s
Stasi (state police) as a means of maintaining political control over
its citizens. The Stasi referred to the tactics as “zersetzen” (German
for “corrode” or “decompose” – a reference to the intended
psychological, social, and financial effects upon the victim).
The
use of tactics such as electronic surveillance, slander, blacklisting,
and psychological operations (“psyops”) methods for counterintelligence
purposes – for example, to punish or suppress dissenters and
whistle-blowers – has a well-documented history in the U.S. and other
nations. For example, in addition to their use by the Stasi, some of the
same tactics were used against American citizens during the infamous Cointelpro operations by the FBI, and the Project MK Ultra experiments by the CIA.
In
gang stalking, the victim is systematically isolated and harassed in a
manner intended to cause sustained psychological torture while creating
the least-possible amount of evidence of stalking that would be visible
to others. Accomplices – such as neighbors, co-workers, and even friends
or relatives of the victim in some cases – are recruited to participate
(often unwittingly) by counterintelligence personnel using various
means, such as by telling them that the target is a potential threat or
that the target is the subject of an “investigation.”
A
whole set of psychological operations tactics is used against targeted
individuals. These methods, described in detail in the overview below,
include such things as threats, verbal harassment, slander, vandalism,
abusive phone calls, computer hacking, tormenting the victim with noise,
and “mobbing” (orchestrated verbal harassment by strangers, neighbors,
or co-workers).
Harassment
tactics used in organized stalking (“Cointelpro Version 2.0″) are
specifically chosen for their lack of easily-captured objective
evidence. Perpetrators use common annoyances such as constant noise by
neighbors or rude comments and behavior by strangers, but on a frequent
ongoing long-term basis. The cumulative effects of relentless exposure
to such tactics can amount to psychological torture for the victim.
Accounts
by numerous victims share common specific details – suggesting that the
perpetrators of gang stalking are following a well-tested and
standardized playbook. Using inconspicuous and difficult-to-prove
tactics – sometimes referred to as “no-touch torture” helps keep
organized stalking off the radar of potential witnesses and the
mainstream news media.
Disinformation
Another
factor contributing to the low profile of organized stalking in the
media is a disinformation campaign – a common tactic in
counterintelligence operations. In the case of organized stalking, the
disinformation is mainly intended to mitigate exposure of the program.
Toward
that end the Internet has been flooded with websites and forum comments
about gang stalking that falsely purport to be from self-proclaimed
victims of organized stalking, making irrational claims – references to
demons and such. The intended effect is to convey the impression that
everyone who claims to be targeted by gang stalking is simply
delusional.
An
additional disinformation strategy has been the establishment of front
groups – most notably, FFCHS (Freedom From Covert Harassment and
Surveillance) – ostensibly a gang stalking victims support group, but
actually an organization run by counterintelligence operatives.
News Reports About Gang Stalking
Mainstream
news media reports about (post-Cointelpro and post-Stasi) gang stalking
– in America and abroad – did not begin to appear until the past decade
or so. Such reporting is still uncommon, but the frequency of reports
by reputable sources has increased dramatically in recent years.
A Newsweek/Daily Beast article in August 2000 described
a trend of systematic intense harassment of individuals in their
workplaces as part of a phenomenon known as “mobbing” – which is
commonly reported by victims as an element of organized stalking.
In
the years following the 9/11 terrorist attacks, mainstream news media
reports about domestic spying in the U.S. began to appear. In2004, the PBS news program NOW and Newsweek magazine
reported that the Pentagon had quietly resumed its practice of domestic
surveillance. (Spying on civilians by the U.S. Army had been one of the
scandals which led to the famous Church Committee investigations by
Congress in the mid-1970s.)
The U.K. newspaper The Sunday Times published an article in October 2004 about the use of gang stalking tactics (“zersetzen”) by the intelligence agency MI5 to punish whistle-blowers.
In May 2006 The Globe and Mail,
a Canadian national newspaper, reported that the Canadian Security
Intelligence Service (CSIS) and the Royal Canadian Mounted Police (RCMP)
used gang stalking techniques (referred to as “Diffuse and Disrupt” tactics) against terrorism suspects for whom they lacked sufficient evidence to legally prosecute.
The July–September 2006 edition of Revue Internationale de Criminologie et de Police technique et scientifique featured
a peer-reviewed academic article by Belgian criminologist Nicolas
Desurmont which described how a secret policy of criminal stalking
sanctioned by law enforcement authorities is used as an extrajudicial
counterintelligence weapon to psychologically terrorize targeted
individuals. Desurmont has since published additional papers on the
subject, and presented his findings at international conferences on
criminology.
A newspaper article in the Verona-Cedar Grove Times in March 2009titled
“Stalker Claims Unsettle Police” described how a self-proclaimed target
of gang stalking had been distributing flyers in his former
neighborhood in Verona, New Jersey, warning about organized stalking of
targeted individuals. The flyers stated: “Their intention is to murder their target without getting their hands dirty. It’s the perfect hate crime.”
In October 2010, the progressive political blog, Daily Kos posted a claim that zersetzen tactics are being used by intelligence agencies in the U.S., the U.K., and Canada.
Two news reports in 2011 described
gang stalking operations in California. In January of that year, local
TV news broadcasts on KION (Channel 46) and KCBA (Channel 35) featured a
report about gang stalking – referred to as such by the reporters and
by Lieutenant Larry Richard of the Santa Cruz Police Department. In
August, San Joaquin Valley newspaper The Record and KCRA (Channel
3) local TV news reported that the city manager of Stockton, California
had been systematcially stalked by local police after a break-down in
contract negotiations between the city and the police union.
An article in the Sun Sentinel, a Pulitzer Prize-winning newspaper in Florida, appeared in December 2012 about
the organized stalking of a police officer by other officers and
sheriff’s deputies from multiple jurisdictions. The victim of the
stalking had cited an off-duty police officer for reckless driving. The
stalking – which included illegally snooping on the victim’s private
data and efforts to harass and intimidate her – was apparently done in
retaliation.
The
brazen use of gang stalking tactics for personal vendettas by law
enforcement personnel in the Stockton, California and Florida cases seem
to suggest that the officers involved were familiar with the
effectiveness of the methods and were also used to getting away with
such behavior.
At least two articles in 2013 alleged that the FBI’s infamous Cointelpro operations have re-emerged in full force. In January, an article inCounterPunch magazine asserted that “Cointelpro is alive and well.” In June, an article in the Nation (America’s
oldest continuously-published weekly magazine) examined the case of
journalist Barrett Brown. He currently faces a potential jail sentence
of 105 years in connection with his efforts to expose the activities of
private security/intelligence firms. The article’s author wrote: “One might think that what we are looking at is Cointelpro 2.0 – an outsourced surveillance state – but in fact it’s worse.”
The cover article of the October 2013 issue of the magazine Fortean Times was
about “State-Sponsored Gangstalking” in the U.S. The author – a
professor at California State University Long Beach – explored the case
of a former U.S. military service member who stole some equipment and
information from the U.S. military, and was then targeted for long-term
intense harassment using psychological operations tactics and electronic
weapons.
A local TV news report in November 2013 on
WDTV Channel 5 (a CBS affiliate in West Virginia) presented a report on
“organized stalking.” The broadcast featured testimony from two
individuals from Pennsylvania who appeared to be credible and sincere,
discussing their constant harassment by perpetrators using gang stalking
tactics.
In December 2013 CBS, the Daily Mail,
and other sources reported that a U.S. government contractor had filed a
federal lawsuit against multiple federal agencies for gang stalking him
(the complaint referred to gang stalking as such).
Scope of Operations
According
to crime survey statistics (linked below) from the U.S. Department of
Justice (DOJ) obtained by a Freedom of Information Act request, in 2006
there were an estimated 446,790 stalking incidents involving three or
more perpetrators stalking a single individual. Of those incidents, it
was estimated – based on victims’ reports – that at least 40 percent
involved apparent coordination of the stalking among the multiple
perpetrators.
Such
statistics suggest the existence of activities whose scope cannot be
explained simply as stalking by criminals – especially given that the
otherwise-comprehensive index of crime categories in the DOJ’s website
conspicuously makes no mention of this type of stalking.
An Internet search-engine query of the term “gang stalking” – as of October 2013 – yields well over six million results.
Many of those references are obvious examples of deliberate
disinformation (as mentioned above, and explored in detail in the
overview below).
Organizational Structure of Counterintelligence Operations
The
FBI ran a secret illegal counterintelligence program (“Cointelpro”) in
the U.S. from 1956 until it was exposed by civilian activists in 1971.
The program mainly targeted political dissidents. Apparently, a more
sophisticated and larger scale counterintelligence program is now in
effect.
Assuming
that Cointelpro operations were in fact suspended after the U.S.
Senate’s Church Committee investigations into the scandal in the 1970s,
evidence suggests that they resumed a short time later. Ted L.
Gunderson, a former high-level FBI official who became a whistle-blower,
asserted that a much more sophisticated version of Cointelpro began to
re-emerge in the 1980s. A link to Gunderson’s affidavit on the subject
is provided in the overview below.
Based
on news reports, accounts of self-proclaimed victims, and the DOJ
statistics cited above, the apparent sophistication and scope of current
organized stalking operations would require the acquiescence of
multiple federal and local government agencies (including the FBI and
the Department of Justice, among others). Federal law enforcement
agencies, America’s 16 intelligence agencies, and local police
departments now share crime and national security information via a
nationwide network of “data fusion centers” – part of the extensive
post-9/11 homeland security infrastructure.
Numerous
job listings by intelligence/security contractor corporations for
“surveillance role players” with active security clearances and training
in counterintelligence (links and details in the overview below)
strongly suggest that federal law enforcement agencies have largely
outsourced these operations – which would be consistent with other
security programs. A June 10, 2013 article in USA Today noted that about 1.4 million Americans have top-secret security clearances.
Federal
and local law enforcement agencies – as well as intelligence agencies –
also make extensive use of criminal informants (who are in large supply
in America, with its extraordinary per capita incarceration rate). It
would be natural for such informants to be used in a counterintelligence
program. Indeed, the original Cointelpro was found by the U.S. Senate’s
Church Committee investigations to have delegated some activities to
organized crime groups. First-hand accounts of self-proclaimed victims
of gang stalking support this assumption: by their appearance and
behavior, many street-level perpetrators seem to be ex-convicts.
A
national counterintelligence program would require acquiescence by the
DOJ – just like the first Cointelpro did. U.S. Attorney General Robert
F. Kennedy approved some of the Cointelpro operations.
Target Selection
Gang stalking apparently targets American citizens deemed to be dissidents or whistle-blowers (and perhaps potential dissidents
and whistle-blowers), although others might be targeted for other
reasons – such as for experimental or training purposes. For
perspective, it should be remembered that for two decades the CIA
performed secret illegal experiments on U.S. and Canadian citizens (the
infamous MK Ultra program). Those experiments included physical and
psychological torture.
It
is entirely possible that some people targeted by America’s
counterintelligence program are chosen simply because they crossed
someone (or a corporation) connected with the program who is exploiting
the counterintelligence system as a personal or corporate weapon. The
intelligence industry no doubt has its share of the sort of opportunists
who would abuse the enormous secret powers available to them.
An example of this occurred in April 2012, when USA Today reported that one of their reporters and an editor were
slandered by a secret disinformation campaign waged by an intelligence
contractor firm to discredit them because the newspaper had investigated
and reported on that contractor (a company which conducted propaganda
campaigns for the U.S. military). Similarly, in August 2013 it was
reported that at least a dozen National Security Agency (NSA) employees
had used their surveillance system access to spy on their current and
former spouses and partners.
Implications
In
addition to being morally reprehensible, gang stalking – just like the
original version of the FBI’s Cointelpro operations – is illegal. It
violates criminal laws in all fifty states against stalking, as well as
grossly violating the U.S. Constitution’s prohibitions against
unreasonable searches and punishment without a trial.
While
the vast majority of Americans are never personally targeted by gang
stalking, they should still be concerned about the existence of such
programs. Even if secret extra-judicial punishment were constitutionally
legitimate (clearly it is not), it would still have an enormous
potential for abuse as a personal or political weapon by its
practitioners.
Ending
this abhorrent practice by law enforcement agencies, intelligence
agencies, and their parasitic corporate contractors will require
exposing what is happening to the public. For anyone reading this, if
you can assist with that exposure – even by simply sharing this
information with relatives and friends – please do so.
All of the above information is explained in greater detail – with links to supporting material – in the overview which follows.
__________________________________________________________
2. Introduction to the Full Explanation of Gang Stalking
I
urge readers to consider the evidence presented here in its totality;
the nature of organized stalking – by design – is such that it is
difficult to comprehend and evaluate without considering it in its full
context.
With
the goal of providing some of that context, the first page of this
website (“Gang Stalking News”) includes not only the relatively
infrequent mainstream press articles specifically about gang stalking,
but also news which is only indirectly related. Published news and
analysis of subjects such as government secrecy, police corruption,
privacy, surveillance, private investigators, and various government
scandals are relevant to organized stalking in ways which I try to make
clear.
I
hope readers are not put-off by my sometimes harsh views on related
political topics. I express my opinions here candidly, and the intensity
of my rhetoric is partly a function of having been on the sharp end of
gang stalking for years.
As
for my analysis of organized stalking, I try to be as measured and
cautious as possible while still confronting the reality that the
subject requires a certain amount of speculation because of the secrecy
and deception which surrounds it.
Given
the current state of technologies and government policies concerning
surveillance, the average American faces many potential and actual
invasions of privacy. For individuals targeted for gang stalking, the
situation is infinitely worse. Given all of that, this website is only
nominally “anonymous.”
Anyone
associated with the professional news media who is interested in
additional information about my personal experiences with gang stalking
can reach me at the email address I have provided.
Thank you for taking an interest in this material.
For victims of gang stalking, I hope that the information I post here will be helpful.
Definitions
Counterintelligence is the assessment
and countering of threats posed by enemy subversion, espionage, and
sabotage. Counterintelligence efforts include tactics such as covert
surveillance (spying on the enemy), sabotage (disruption of the enemy’s
activities), and disinformation (efforts to deceive the enemy and – when
it serves the objectives of the counterintelligence program – the
public).
Wikipedia’s entry on counterintelligence describes the organizational nature this way:
“In
most countries the counterintelligence mission is spread over multiple
organizations, though one usually predominates. There is usually a
domestic counterintelligence service, usually part of a
larger organization such as the Federal Bureau of Investigation in the United States.”
Cointelpro (short
for “Counterintelligence Program”) was the name of a secret illegal
counterintelligence program run by the FBI from 1956 until it was
exposed by civilian activists in 1971 and subsequently investigated by
Congress.
The
U.S. Senate’s Church Committee investigations in the mid-1970s found
that under Cointelpro U.S. law enforcement personnel and their various
government and private citizen and criminal accomplices systematically
spied on, slandered, terrorized, and committed acts of violence
(including murder) against American citizens deemed to be dissidents.
Gang stalking (also known as “organized stalking”) is
the covert organized surveillance and harassment of a targeted
individual by multiple perpetrators. The goal is to systematically
isolate and harass the victim using tactics whose cumulative effects
amount to psychological torture.
As
far as I know, the term “gang stalking” has not yet found its way into
any major print publication dictionaries – which is not surprising for a
subject residing in the grey area of counterintelligence. The term is
however, much less obscure than it was, say a decade ago. For example,
you can find it here in the (non-censored) popular online dictionary of slang terms:
the Urban Dictionary.
Organized
stalking of a targeted individual employs methods used in
counterintelligence operations – such as electronic and human
surveillance, slander, disinformation, and a variety of intensive
long-term psychological operations (“psyops”) methods.
The Stasi (the
infamous state police agency that monitored and terrorized citizens in
communist East Germany by infiltrating the society with spies) referred
to these tactics – aimed at breaking-down targeted individuals as “zersetzen” which translates roughly as “to decompose or to corrode.”
Although
less common than “gang stalking,” the term “organized stalking” is
probably a better description since it more accurately conveys the
systematic nature of what is being done; also it does not create the
erroneous impression that the activity is related to street gangs.
Other terms used to describe stalking by multiple perpetrators include“group stalking,” “vigilante stalking,” and “cause stalking.” The latter term refers to the fact that the activity is sometimes associated with political causes.
For example, in his book
Stopping a Stalker,
Robert L. Snow, a retired police captain from the Indianapolis Police
Department, devoted a chapter to organized stalking by multiple
perpetrators associated with causes – such as stalking of abortion
clinic staff members by extreme anti-abortion activists, and stalking of
workers who crossed picket lines by union members.
The Number of Stalking Incidents in the U.S.
According to
U.S. Department of Justice crime survey statisticsobtained
via a Freedom of Information Act request, in 2006 there were an
estimated 446,790 stalking incidents involving three or more
perpetrators stalking a single individual. Of those incidents, it was
estimated – based on victim reports – that at least 40 percent
apparently involved coordination of the stalking among the multiple
perpetrators.
An
attorney, Keith Labella, contacted the National Center for Victims of
Crime (which is funded by the DOJ) in October 2008 to inquire about the
frequency of reports the center receives about organized stalking
crimes. He was informed that they receive “thousands of calls per
month.”
Notwithstanding
the frequency of calls to their helpline, the center offered no
guidance or referral to other agencies or organizations. Here is
Mr. Labella’s affidavit about his inquiry.
Cointelpro Version 2.0
In
a society as heavily-policed as America now is – a society whose
National Security Agency is tracking everyone’s phone calls and Internet
activity for example – it is inconceivable that tens of thousands or
more cases of criminal stalking (as documented in the DOJ crime
statistics) fail to appear on the radar of law enforcement and
intelligence agencies.
Yet
there is no mention of such crimes by the federal government anywhere
except in those statistics (which had to be obtained via a Freedom of
Information Act request).
The
implication is inescapable: federal agencies are acquiescing in what is
happening. Assuming the statistics are even roughly accurate, there is
no other explanation; organized stalking (the monitoring and
“disruption” of the activities of targeted individuals) is being
perpetrated as part of a counterintelligence program.
Under the Radar
How is it that the general public would not be aware of this phenomenon?
There are five main reasons:
(1) Covert Methods
The
primary explanation for the low-profile of gang stalking is that
counterintelligence operations are performed covertly. I describe the
tactics in detail later in this overview, but the main point is obvious:
just like the FBI’s original (and equally illegal) version of
Cointelpro, law enforcement and intelligence agencies are not going to
advertise what they are doing.
(2) Psychological Explanations
Tactics
developed by the Stasi in East Germany and currently used by the FBI in
America are diabolical – there is no other word – in that reports of
the harassment will be naturally dismissed by most people as examples of
paranoia.
Victims’
accounts tend to be dismissed since their experiences sound like
commonplace occurrences – because that is indeed what they are:
strangers who are rude, neighbors who are noisy, businesses which
deliver bad service, drivers who cut-off the victim in traffic,
pedestrians who bump them as they walk by, etc. These are things which
happen to everyone. But for gang stalking victims, these things happen constantly – which becomes a form of real psychological torture, the intensity of which must be experienced to comprehend.
Using
such tactics produces three desirable results from the perspective of
the perpetrators: (a) the victim’s reports will not be taken seriously;
(b) the victim will become angry about not being believed; and (c) the
victim’s credibility will be undermined.
(3) Ignorance
Americans
are largely unaware of the history of well-documented relevant
programs, such as the FBI’s Cointelpro operations and the CIA’s MK Ultra
program – even though both were thoroughly investigated and exposed by
Congress in the 1970s. Similarly, although many people have heard of the
Stasi (East Germany’s secret police agency), they are not specifically
familiar with the Stasi’s use of zersetzung – which was a set of methods
virtually identical to current gang stalking in America.
Of
course, even well-educated individuals would be unlikely to recognize
the connections between a local situation in which they are told a
neighbor or co-worker or business patron is under investigation and the
relatively-obscure historical predecessors of gang stalking.
(4) Cowardice, Laziness, & Incompetence in the Mainstream News Media
Organized
stalking goes mostly undiscussed in the mainstream news media. There
are some notable exceptions – most frequently in the local and
alternative press. I review those in detail throughout this website, but
as a rule, major corporate news agencies avoid discussing matters which
the intelligence and law enforcement community do not wish to have
discussed.
This
silence in the press is largely the result of the kinds of
self-censorship documented in sources such as Kristina Borjesson’s
Into the Buzzsaw, and Noam Chomsky’s
Manufacturing Consent.
(5) Disinformation
Search
results on the Internet’s largest search engine, Google, fluctuate
wildly for particular words and phrases over time. Only people within
Google know the exact policies and algorithms which determine those
results, but the search results do provide a rough indication of the
online presence of certain topics.
Typically,
the list of websites generated by a search is the tip of an iceberg.
Ten pages of website links will show the top 100 results, but the screen
also displays a much larger number that indicates the number of
references to the search term that were detected.
A Google query of the term “gang stalking” in October 2013 yielded over six million results.
As
you begin to wade through the search results, you will mostly encounter
websites filled with incoherent rubbish. Anyone even superficially
familiar with counterintelligence will recognize this tactic; it is
called disinformation.
This
is another reason organized stalking has been able to remain mostly
below the public’s radar. Disinformation is used to muddy the waters
surrounding the topic wherever it is discussed online. The intent is to
mitigate exposure of the operations.
Because
of its central importance to counterintelligence generally – and
organized stalking in particular – I explore the subject of
disinformation at length in its own section of this overview and
elsewhere in this website.
Allegations of Organized Stalking by Private Organizations
Gang
stalking tactics are sometimes alleged to be used by certain fraternal
orders such as Freemasons, and by various religious groups such as
Scientologists and Jehovah’s Witnesses – for example, to control or
punish current or former members. See for example, the
March 15, 2013 article about that in the “Gang Stalking News” section of this website.
I
have no first-hand knowledge of the use of organized stalking by
religious groups, but it does seem plausible – especially if you agree
with America’s second president, John Adams:
“There
is a germ of religion in human nature so strong that whenever an order
of men can persuade the people by flattery or terror that they have
salvation at their disposal, there can be no end to fraud, violence, or
usurpation.”
In
the case of Scientologists, there is reportedly a policy called “Fair
Game” under which the church allegedly uses aggressive tactics toward
individuals and groups it perceives as its enemies. The practices – as
described in
this 1990 Los Angeles Times article,
apparently include some tactics associated with organized stalking:
“psychological warfare,” “dirty tricks,” and “harassment.” Reportedly,
the Fair Game policy also sometimes involves employing detectives,
former police officers, and criminals:
“Teams
of private detectives have been dispatched to the far corners of the
world to spy on critics and rummage through their personal lives–and
trash cans–for information to discredit them.
During
one investigation, headed by a former Los Angeles police sergeant, the
church paid tens of thousands of dollars to reputed organized crime
figures and con men for information linking a leading church opponent to
a crime that it turned out he did not commit.”
Instances
of “cause stalking” and stalking by religious cults presumably account
for only a very small portion of the numerous incidents in the
aforementioned crime survey statistics. It is true however, that members
of religious cults (and cult-like fraternal organizations) are – by
definition – easily manipulated, so they could serve in some cases as
“useful idiot” vigilantes for others whose motivations they don’t even
comprehend.
That
is perhaps true for most of the general public since most people are
completely unaware of the existence of any domestic counterintelligence
operations and would be unlikely to suspect that what they are being
told might be disinformation and manipulation as part of a modern
American version of the Stasi.
Lowering Requirements for Investigations
In
2008 the U.S. Department of Justice guidelines which govern FBI
investigations were changed to create a new category of investigation
called
“assessments.” These
investigations can be initiated with no evidence that any criminal
activity has occurred, and the investigations can involve such intrusive
measures as physical surveillance, recruitment of criminal informants,
interviewing associates of the person being investigated and deploying
undercover FBI agents.
Exploiting a Government Program as a Private Weapon
The
potential for abuse of power by members of private intelligence
corporations and government agencies in all of this is enormous.
Here is an example of such abuse which was reported in the news media – partly because it was directed at
members of the news media. One of the counterintelligence tactics which
the federal government hires intelligence contractors to perform is
spreading disinformation. Most Americans would probably be surprised to
learn that systematically spreading lies is even a government contractor
job which their taxes are funding, but they underestimate – despite
President Eisenhower’s famous warning – the extent to which the U.S.
government’s defense budget has become a pig trough for shady
contractors.
If you criticize a comedian, you will likely become the target of a joke. Similarly, when a reporter and editor at USA Today investigated and reported on the U.S. propaganda industry in 2012, they were anonymously slandered by those same contractors.
This was the opening paragraph of
their first report that apparently did not go over well with the businesses they were exposing:
“
As the Pentagon has sought to sell wars in Iraq and Afghanistan to
often-hostile populations there, it has spent hundreds of millions of
dollars on poorly tracked marketing and propaganda campaigns that
military leaders like to call “information operations,” the modern
equivalent of psychological warfare.”
As a result of their reporting, this is what happened:
“Fake
Twitter and Facebook accounts have been created in their names, along
with a Wikipedia entry and dozens of message board postings and blog
comments. Websites were registered in their names….”
“…Internet
domain registries show the website TomVandenBrook.com was created Jan. 7
— just days after Pentagon reporter Tom Vanden Brook first contacted
Pentagon contractors involved in the program. Two weeks after his editor
Ray Locker’s byline appeared on a story, someone created a similar
site, RayLocker.com, through the same company.”
The article notes
that a proxy service was used to hide the identity of the owner of the
websites, and a third website was registered to a non-existent address.
Slander
is just one of the tactics used in organized stalking by
counterintelligence operations. Any or all of the tactics – which are
described in detail in a section of this overview – could be used as a
weapon by people in the business.
In
theory, an organized stalking operation against an individual could be
initiated by anyone familiar with the tactics who has associates willing
to participate. Perpetrators with financial resources could easily
employ private investigators, for example, and others with relevant
technical skills to wage a sophisticated operation against someone for
revenge or intimidation.
Someone
with connections to current or former law enforcement or intelligence
agency personnel – or military personnel with a background in
intelligence – could mount a very serious campaign against a victim
without even (officially) involving government agencies in the initial
stages of the investigation and harassment.
In
a tactic called “baiting” a surveillance operation can selectively
capture evidence of a targeted person responding to harassment. That
evidence could then be used to justify the initiation of more formal
scrutiny by a government agency.
At
whatever point at which it becomes useful or necessary, the
perpetrators can – officially or unofficially – turn over to the
government counterintelligence personnel whatever they have gathered to
have the individual targeted more formally. For example, they could
contact a
“Terrorism Liaison Officer” (TLO) –
a government or civilian operative entrusted with hunting for
“suspicious activity.” More on TLOs in section 10 below (“The
Organizational Structure of Gang Stalking”).
In
essence, organized stalking tactics (and a national counterintelligence
program which uses such tacics) could easily be exploited – and
probably are – as a weapon against individuals who are disliked for any
reason by someone who is either a member of the community of
intelligence/security firms, law enforcement agencies, and intelligence
agencies. Similarly, being a member of the FBI-corporate alliance
called InfraGard (discussed in detail below) could create a perfect opportunity to have someone blacklisted.
Being
associated with the national counterintelligence program of organized
stalking (“Cointelpro 2.0″) is like having a cousin who is in the Mafia.
The Spy Industry and the Threat to American Democracy
“In
the councils of government, we must guard against the acquisition of
unwarranted influence, whether sought or unsought, by the military
industrial complex.” – President Dwight D. Eisenhower
In
addition to the extreme violations of the Constitutional and state
rights of the particular individuals targeted for organized stalking,
the current counterintelligence program poses a threat to democracy
itself, since it can be used against anyone who dares to question the
legitimacy of the government’s authority.
The
FBI’s original Cointelpro operations were illegal and disturbing abuses
of power; the modern version is similarly corrupt, and it is supported
by the now-vast network of powerful secretive agencies and contractors
armed with much more powerful technology.
The
huge (and largely secret) federal budget for intelligence activities
and homeland security supports a large industry of private contractors
who provide technology and services for surveillance, investigations,
security, and varous intelligence functions.
About 70 percent of America’s budget for intelligence activities goes to private contractors, and nearly one-quarter of the 4.9 million people who hold security clearances work for private firms, according to
a 2012 report from the Director of National Intelligence.
The
collusion between corporations and the federal government in the area
of domestic surveillance is inherently dangerous. This
July 2013 article in the Atlantic posed the issue this way:
Government
and corporations are both capable of terrible things. To have them
colluding with one another in secret, inexorably arranging things so
that there’s disincentive for disagreement among them, is terrifying.
The people can fight Big Government. The people can fight Big Finance.
The people can fight Big Tech. Could the people fight them if they’re
all working together with secret law on their side? Booz Allen Hamilton
is paid handsomely to spy on us for the government, then pours campaign
contributions back into that same government, protecting their powerful
financial incentive to have the surveillance state expand, something
that is already a bipartisan cause.
Political
support for a Stasi Big Brother police state in the U.S. is partly
rooted in hawkish views about law enforcement and anti-terrorism
strategy, but it’s largely rooted in greed.
Spying on Americans is a lucrative business for intelligence-security contractors.
When
Congress voted in July 2013 on whether to rein-in the NSA’s domestic
surveillance program which tracks Americans’ phone calls and emails,
House members who voted to continue the surveillance
received twice as much campaign finance money from
the military and intelligence industry as those who voted to dismantle the program.
Americans
are not normally permitted to know how much of their money the federal
government spends on spying. NSA whistle-blower Edward Snowden changed
that.
Defenders of Constitutional liberties are up against a powerful and well-financed industry of parasites.
This May 2013 article in
The New Yorker describes a “bureaucratic empire” of entities built around the homeland security industry:
“When
the Washington Post surveyed that empire, in 2010, it counted more than
three thousand government organizations and associated private
companies working on counterterrorism, homeland security, and
intelligence, in ten thousand locations across the United States.”
The
whole thing is interesting, but if nothing else, watch the set-up
(minutes 3 to 6) and the five minutes or so in the middle (minutes 27 to
32) about journalists uncovering the massive shadowy industry of
private intelligence firms.
“It
has essentially merged with a set of crony outfits that now do a
significant part of its work. It has hired private contractors by the tens of thousands, creating corporate spies, corporate analysts, corporate mercenaries, corporate builders, and corporate providers for a structure that is increasingly becoming the profit-center of a state within a state.”
Barrett Brown on the role of Private Intelligence/Security Contractors
As
I am updating this (in November 2013), journalist Barrett Brown is in
jail facing charges related to his role in exposing information leaked
by hackers who obtained internal emails from private intelligence firms,
such as Stratfor and HBGary.
Activities
revealed in those leaked emails included things such as plotting to
discredit journalist Glenn Greenwald and critics of the Chamber of
Commerce by spreading lies about them.
In
other words, at least some of these numerous secret firms engage in the
kind of actions which the CIA might perform against foreign enemies –
but they do so on behalf of corporate interests.
Job Ads for Gang Stalkers?
On August 21, 2013 Drudge Report linked to a brief article posted the day before on InfoWars about a job announcement posted in San Diego. The job – advertised on Craigslist – was for a part-time position with an intelligence/security contractor firm as a “surveillance role player.”
As I explain in detail
here (along
with a link to the article and copies of similar job ads from other
contractors), these job listings are numerous, but they are mostly found
on on the websites of intelligence/security firms. You can locate them
by performing an online search for “surveillance role player job.”
Clearly
these jobs are for some type of domestic spying (there are no foreign
language requirements, for example). All of the job listings specify
that applicants must have active secret clearances andcounterintelligence training.
As
of this writing (October 2013), I have been unable to locate any
mainstream news reports that might shed light on this issue, but
multiple indications suggest that these could be jobs for gang stalkers.
I re-visit this critical issue in section 11 of this overview (“The
Organizational Structure of Gang Stalking”).
Here is an example of one such job listing:
Click on image to enlarge.
Law Enforcement & Intelligence Agencies’ Support of a Corporate Agenda
That report describes two main entities which facilitate that partnership:
“There
are two primary domestic public-private intelligence sharing
partnerships at work at the federal level: InfraGard and the Domestic
Security Alliance Council (DSAC).
InfraGard is
a public-private intelligence sharing partnership managed by the FBI
Cyber Division Public/Private Alliance Unit (PPAU). As described by the
FBI, Infragard is an “association of businesses, academic institutions,
state and local law enforcement agencies and other participants
dedicated to sharing information and intelligence to prevent hostile
acts against the United States.” There are 86 Infragard chapters
nationwide. These Infragard chapters serve as representatives of private
sector “stakeholders” in many of the nation’s fusion centers.
DSAC is
a public-private intelligence sharing partnership between the FBI, U.S.
DHS I&A and several of the nation’s leading corporate/financial
interests. Some of these corporate/financial interests comprise the DSAC
Leadership Board. The DSAC Leadership Board consists of 29 corporations
and banks, including several entities that have been the subject of OWS
protests/criticism. Corporate/financial interests active in the DSAC
Leadership Board include: Bank of America, MasterCard, Citigroup,
American Express, Barclays, RBS Citizens, 3M, Archer Daniels Midland,
ConocoPhillips, Time Warner and Wal-Mart. Along with DSAC chairmen from
the FBI and U.S. DHS I&A, DSAC is co-chaired by a representative of
these private sector interests– currently Grant Ashley, vice president
of global security for pharmaceutical giant Merck & Co.”
For a fascinating look at InfraGard, watch
this episode about
that subject from a TV series hosted by Jesse Ventura. The host
immediately recognizes the potential for abuse of power by members of
this secretive powerful group, and confronts several leaders about it on
camera.
The March 2008 issue of The Progressive featured
an article about this creepy corporate spy club. It seems that
InfraGard’s communications with the FBI and Homeland Security are not a
matter for the public to know about, as they are covered by the “trade
secrets” exemption of the Freedom of Information Act.
Apparently
mindful that the public will be naturally suspicious of the
organization’s legitimacy, InfraGard’s website explains that members
must carefully manage the image presented to the public:
“The
interests of InfraGard must be protected whenever presented to
non-InfraGard members,” the website states. “During interviews with
members of the press, controlling the image of InfraGard being presented
can be difficult. Proper preparation for the interview will minimize
the risk of embarrassment. . . . The InfraGard leadership and the local
FBI representative should review the submitted questions, agree on the
predilection of the answers, and identify the appropriate interviewee. .
. . Tailor answers to the expected audience. . . . Questions concerning
sensitive information should be avoided.”
For
those wishing to join this elite secretive alliance between the FBI and
the corporate sector – to learn their secret handshake and to gain the
power of being able to name an employee as a suspicious person to be
targeted by federal goons, you “must be sponsored by an existing InfraGard member, chapter, or partner organization.”
The
existence of programs like InfraGard, along with the FBI’s infiltration
of groups like Occupy Wall Street, and the plotting by intelligence
firms to wage a disinformation-slander campaign against critics of the
Chamber of Commerce (also discussed in this overview), all suggest that
activist and hacker Jeremy Hammond is correct in his assessment of the
current U.S. law enforcement industry personnel – namely, that they are “the boot boys of the 1 percent, paid to protect the rich and powerful.”
Artist’s rendering of a typical InfraGard member
A Gang Stalking Organization Chart
Victims
of organized stalking can only speculate about the exact nature of the
shadowy network of perpetrators arrayed against them.
That
speculation is made more difficult by the fact that the people who are
overtly and covertly watching them and perpetrating various acts of
harassment are of different classes of perpetrators with different
motivations and have different connections (and often no connection) to
the victim.
For
example, the street-level perpetrator (“perp” as cops say) is typically
someone who appears to be a rough-looking homeless or near-homeless
ex-con type.
Their
interactions with the target require no technical skills; the perp is
just following some simple instruction – for example, to bump into the
victim, or to make some specific creepy comment, or to harass the victim
at his or her residence by making various noises.
Such
participants in the stalking of course would not be told anything about
who they are ultimately working for; in some cases perhaps they are
simply paid a small sum of cash by a person who approached them on the
street to perform a single act of harassment. In other cases, they might
be ex-con’s who have been recruited/coerced/paid to function –
technically – as “criminal informants.”
At
a slightly higher level in the stalker food-chain (among those who
interact with the victims) are people who appear more clean-cut and are
often carrying a cell phone – presumably to communicate with their
handlers.
Some
of the intermediate-level participants are apparently recruited because
of their relevant technical skills or because their jobs afford them
access to facilities and information relevant to the operation – such as
phone technicians, security guards, and landlords.
At
the level above them are the people who actually orchestrate the
operation. Based on my own observations, analysis, speculation, and
various material I’ve read (which is included or linked in this
website), these people are presumably employed by various intelligence
contractors who are ultimately overseen by federal law enforcement
and/or intelligence agency personnel.
The
active support – or at least approval – of federal law enforcement and
intelligence agencies would be necessary for such activities to occur
without attracting interference from the massive homeland security
infrastructure now in place.
Precedence for Organized Stalking of Dissidents
Such
conspiratorial criminality might seem far-fetched if not for the fact
that the U.S. government has been caught doing such things before.
Context provided by an awareness of documented crimes – past and present
– by government agencies is critical for evaluating the plausibility of
claims about organized stalking in the U.S.
________________________________________________________
3. Crimes by U.S. Law Enforcement & Intelligence Agencies
“When the president does it, that means it is not illegal.”– Richard Nixon in a 1977 interview with David Frost
Attitudes of Government Officials About the Law
Although
scandals such as Watergate and Iran-Contra occasionally break into the
public’s consciousness, most Americans are unaware of the criminality
which routinely occurs at the upper levels of government.
The
same government officials who oversee America’s domestic surveillance
and law enforcement programs often have a very casual attitude about
their own obligation to obey the law.
In a Senate hearing in March 2013 the Director of National Intelligence, James Clapper, was asked “Does the NSA collect any type of data at all on millions or hundreds of millions of Americans?”Clapper said they did not.
NSA
whistle-blower Edward Snowden’s subsequent revelations proved that
Clapper was lying to Congress – which Clapper himself was forced to
acknowledge. A typical American citizen would be prosecuted for perjury
if he or she lied to Congress; Clapper obviously has no such concerns.
As
a practical matter, intelligence agencies and federal law enforcement
agencies exist in a mostly secret and politically-protected realm
outside of the laws that bind the rest of us. They know they won’t be
punished for their crimes.
The
political establishment is similarly unconcerned. Since the
intelligence and law enforcement community enjoys virtually
unconditional support from both major parties, neither party has to
worry about negative political consequences for its role in creating
domestic surveillance programs which violate the Fourth Amendment.
In April 2013
WikiLeaks published
a searchable database of more than 1.7 million U.S. diplomatic and
intelligence documents from the mid-1970s which had been declassified.
The documents included a revealing transcript of a discussion involving
then-Secretary of State Henry Kissinger.
When
a Turkish official suggested that the U.S. arrange to supply military
hardware to Turkey – in violation of a U.S. Congressional arms embargo –
Kissinger joked about the illegality:
Before
the Freedom of Information Act, I used to say at meetings, “The illegal
we do immediately; the unconstitutional takes a little longer.”
[laughter] But since the Freedom of Information Act, I’m afraid to say
things like that.
We’ll make a major effort.
For
the average American, violating federal laws would be a serious matter;
for government officials like Kissinger it is literally a joke.
A
veteran intelligence official with decades of experience at various
agencies identified to me what he sees as the real problem with the
current NSA: “It’s increasingly become a culture of arrogance. They tell
Congress what they want to tell them. Mike Rogers and Dianne Feinstein
at the Intelligence Committees don’t know what they don’t know about the
programs.” He himself was asked to skew the data an intelligence agency
submitted to Congress, in an effort to get a bigger piece of the
intelligence budget. He refused and was promptly replaced in his job,
presumably by someone who would do as told.
Such
behavior at the federal level sets the tone for law enforcement
agencies lower down the food chain. I address this issue also in the
section of this overview about the U.S. Department of Justice (DOJ).
A disturbing example of the “we’re above the law” attitude of some members of local law enforcement agencies is
an event which occurred in Stockton, California in August 2011.
Since the case is a clear example of organized stalking by law
enforcement personnel – and was reported in a newspaper and TV news
report – I include it in the published articles section of this overview
and elsewhere. Please forgive the redundancy.
I
highlight that incident because the circumstances strongly suggested
that the officers involved were familiar with organized stalking tactics
and that they were used to getting away with such illegal harassment
and intimidation.
The Public’s Trust in Authority Figures
A Gallup poll in May 2013 found that nearly half of the country believes that the federal government poses an
“immediate threat” to their rights and freedoms.
Note that this poll was conducted during the month before the
revelation by NSA whistle-blower Edward Snowden that the intelligence
community was secretly spying on the phone call records of all
Americans.
Trust
in U.S. government officials has eroded for two reasons: (1) the
expansion of power and secrecy of the federal government predictably has
led to abuses of authority, and (2) access to information via the
Internet has made it harder to keep such abuses secret.
That’s
the good news for targets of organized stalking. The bad news is that –
as a practical matter – many people still naïvely assume that anyone
who seems to be associated with law enforcement should be absolutely
trusted – as seen in
this ABC TV show segment.
Organized
stalkers (and other criminals) can easily exploit that fact to recruit
accomplices by persuading them that they are assisting an investigation
or a neighborhood watch surveillance program.
Experiments have proven this
strong inclination of people to trust authority figures – and to try to
gain their approval. Since this tendency is relevant to
counterintelligence issues, I address the subject at more length in its
own section of this overview.
Evidence of this sheep-like deference to authority is not limited to the realm of science, by the way.
In January 2014 a
jury in the southern California city of Fullerton decided that it was
OK with them that their local police department beat to death an unarmed
mentally-ill homeless man who posed no risk to anyone. They were not
persuaded by the mere fact that the murder had been captured on
surveillance camera video.
Rise of the Police State
Although
the amount of money the U.S. government spends on intelligence
activities is a secret, it is clear that the monitoring of American
citizens is taken seriously by their government. This is especially
clear after revelations in 2013 about the scope of domestic surveillance
by the National Security Agency (NSA).
Equally
clear is that the U.S. justice system aggressively polices and
prosecutes its citizens: the U.S. has one of the very highest
per capita incarceration rates in the world.
A
common – and accurate – critique of the modern U.S. government is that
it has become unbalanced by the massive expansion of power and secrecy
in the executive branch.
A
related problem is that the now-vast network of federal agencies (whose
officials of course are unelected) operate with minimal accountability.
In many cases they effectively create their own laws.
This
is true to some extent in all agencies since they issue and enforce
regulations, but the potential to be corrupted by power is infinitely
greater in law enforcement and intelligence agencies such as the FBI,
the CIA, and the NSA – which operate mostly in secrecy.
The Frequency of Crimes Perpetrated by Government Agencies
You
don’t have to visit an obscure blog these days to find complaints that
America is becoming something of a police state. But America’s
government doesn’t just engage in secret invasive surveillance and
aggressive policing – it also engages in crimes.
That’s
not my opinion – that’s what the federal government itself says. For
example, the CIA constantly commits crimes according to the House
Permanent Select Committee on Intelligence, IC 21 (April 9, 1996) – as
explained in chapter 6 of
Into the Buzzsaw.
The Congressional report cited therein by John Kelly (whose bookTainting Evidence: Inside the Scandals at the FBI Crime Lab was
nominated for a Pulitzer Prize) states that “several hundred times
every day” officers of the Clandestine Service (CS) of the CIA “engage
in highly illegal activities.”
In an
August 2013 article,
Reuters revealed that – as a matter of official policy – a secretive
unit within the U.S. Drug Enforcement Administration (DEA) instructs law
enforcement officers in various agencies to lie about the origins of
their investigations.
Some
cops don’t need to be told to lie. The subject of crimes by police
officers is generally under-reported in the mainstream corporate news
media – especially on national TV news, but to evaluate the plausibility
of widespread acquiescence in gang stalking by local police officers it
is helpful to consider criminality by police generally.
This review of crimes by Chicago police officers published
by the University of Illinois at Chicago, Department of Political
Science is illuminating. Browse through the list of convictions of
police officers on pages 24 to 47 of this report. The list is in
alphabetical order by the officers’ names, and covers the past
half-century. Keep in mind: these were just the crimes that were
discovered and prosecuted.
The
crimes range from bribery and extortion to torture and murder. Gang
stalking would be like jay-walking for the cops on this list.
Crimes Perpetrated Under Authority of the FBI
Law
enforcement agencies in America make extensive use of criminal
informants in their investigations, and in many cases authorize
criminals to commit crimes when an agency believes it furthers its
goals, as reported for example in this August 2013 article in USA Today.
“The
FBI gave its informants permission to break the law at least 5,658
times in a single year, according to newly-disclosed documents that show
just how often the nation’s top law enforcement agency enlists
criminals to help it battle crime.”
The FBI report from 2011 which USA Today obtained via the Freedom of Information Act does not reveal the nature of the crimes:
“The
report does not spell out what types of crimes its agents authorized,
or how serious they were. It also did not include any information about
crimes the bureau’s sources were known to have committed without the
government’s permission.”
FBI Whistle-Blowers
An October 2013 article in Reason described
the FBI as a “dangerous” domestic spy agency. The author, J.D. Tucille,
explains not only how the FBI is able to mostly keep its agents from
revealing the agency’s crimes, but also why the abuses tend not to be
investigated very aggressively by the press:
“Never hesitant about flexing its muscles to target dissenters and whistleblowers, the FBI….is more dangerous than ever.”
“Exempted
from the Whistleblower Protection Act, the FBI freely retaliates
against employees who attempt to call out wrongdoing. As a result, it’s
rare for FBI employees to speak out. That culture lends itself to a
willingness to target whistleblowers in other agencies—and journalists.”
Tucille quoted from the
September 2013 report by the ACLU –
Unleashed and Unaccountable: the FBI’s Unchecked Abuse of Authority. That report noted examples of the FBI spying on journalists, such as this:
“In
2010 the Inspector General reported the FBI used an illegal ‘exigent
letter’ to obtain the telephone records of 7 New York Times and
Washington Post reporters.”
Famous
Watergate reporter Carl Bernstein said on May 14, 2013 on MSNBC that he
believed that the intention of the AP records seizure was “to intimidate people who talk to reporters.”
Mike German
Mike
German was a decorated FBI agent who specialized in counter-terrorism.
He left the agency after 16 years, when he became a whistle-blower. He
had discovered that fellow officers were violating wiretapping
regulations. When he reported that to his supervisors, his accusations
were ignored, and his career was effectively frozen. Mr. German is now
associated with the ACLU, as a senior policy counsel. Apparently,
his experience was not unique in an agency which values secrecy more than ethics.
Mike German is one of the guests on this
Democracy Now! interviewtogether
with an individual who was targeted by the FBI for being a political
dissident. The individual was subjected to intense investigation for
years – despite having no criminal record, apart from trespassing
incidents related to political protests.
At
2:06 in the video of this interview journalist Amy Goodman asks Mike
German to explain the FBI’s legal authority to perform the “assessments”
which, as I mentioned in the introduction above, are essentially
investigations that can now be launched against an individual without
any evidence that the individual has committed a crime.
Ted Gunderson
As previously mentioned, USA Today found that the FBI frequently authorizes criminals to commit crimes when its officials believe it furthers their objectives.
According
to the late Ted Gunderson, a former high-level FBI official who became a
whistle-blower, the crimes which are partly delegated to criminals
include aspects of organized stalking.
Gunderson claimed that the FBI’s infamous Cointelpro operations (which lasted from 1956 to 1971) re-emerged in a more sophisticated form a decade or so later.
Because
of its enormous prison population – largely associated with the “drug
war” – America has a vast number of ex-convicts who can be easily
coerced or paid to participate in organized stalking. My personal
observations suggest that this is exactly what is being done in many of
the instances of street-level harassment of targeted individuals.
How Far Will U.S. Officials Go in their Criminality?
An instructive example of the extremes to which federal agencies sometimes go is the CIA’s secret MK Ultra program.
I describe MK Ultra in some detail in section 6 below, so I will just
note here that it involved performing experiments (including
psychological and physical torture) on American citizens. No one was
punished for their participation in that program – which lasted two
decades, and the head of the CIA destroyed most of the records about it
when it was discovered.
In
September 1970 the leftists in Chile won a plurality of that country’s
democratic election, as a result of which, their representative would
have soon been confirmed as the next president. Right-wing political
leaders in Chile, some major U.S. corporations which did business in the
country (including Pepsi Cola and Chase Manhattan Bank), and the CIA
were not pleased with this development and communicated that to
then-president Richard Nixon and his Secretary of State, Henry
Kissinger, and they plotted to arrange for a military coup instead.
An
obstacle they faced was that the chief of the Chilean General Staff,
General René Schnieder did not believe in interfering with the
democratic process.
So Nixon and Kissinger had him murdered.
The
incident – and other very serious transgressions – did not prevent
Kissinger from generally being treated with great respect and adulation
by the American news media over the rest of his career. That kind of
sycophancy and complacency by mainstream journalists obviously makes it
difficult to expose and punish the bad behavior done in secret by the
U.S. government.
U.S.
officials are also quite willing to engage in very serious crimes
against their own citizens when they believe it could further their
agendas. A good example of this was “Operation Northwoods.”
A
proposal was drafted in 1962 by the highest-level officials in the U.S.
military establishment to stage “false flag” incidents – covert
operations designed to deceive the public into thinking that acts of
terrorism against Americans were being perpetrated by another country –
in that case, Cuba.
The following is excerpted from a Wikipedia entry on the subject:
Operation Northwoods was
a series of false flag proposals that originated within the United
States government in 1962, but were rejected by the Kennedy
administration.[2] The
proposals called for the Central Intelligence Agency (CIA), or other
operatives, to commit perceived acts of terrorism in U.S. cities and
elsewhere. These acts of terrorism were to be blamed on Cubain order to
create public support for a war against that nation, which had recently
become communist under Fidel Castro.[3] One
part of Operation Northwoods was to “develop a Communist Cuban terror
campaign in the Miami area, in other Florida cities and even in
Washington”.
Operation
Northwoods proposals included hijackings and bombings followed by the
introduction of phony evidence that would implicate the Cuban
government. It stated:
“The
desired result from the execution of this plan would be to place the
United States in the apparent position of suffering defensible
grievances from a rash and irresponsible government of Cuba and to
develop an international image of a Cuban threat to peace in the Western
Hemisphere.”
Several
other proposals were included within Operation Northwoods, including
real or simulated actions against various U.S. military and civilian
targets. The plan was drafted by the Joint Chiefs of Staff, signed by
Chairman Lyman Lemnitzer and sent to the Secretary of Defense. Although
part of the U.S. government’s Cuban Project anti-communist initiative,
Operation Northwoods was never officially accepted; it was authorized by
the Joint Chiefs of Staff, but then rejected by President John F.
Kennedy.
2 – Ruppe, David (May 1, 2001). ”U.S. Military Wanted to Provoke War With Cuba”. ABC News. Retrieved January 21, 2012.
3 – Zaitchik, Alexander (3 March 2011) Meet Alex Jones, Rolling Stone
Lying About Killing
A
thorough review of disturbing crimes and conspiracies by the U.S.
government is beyond the scope of this website. My goal here is simply
to cite a few examples to make the general case that acts and programs
involving serious deception and criminality are not aberrations. Here is
a final example from a few years ago.
When
a U.S. cruise missile struck a village in Yemen in December 2009
killing 41 people – including 14 women and 21 children – the U.S.
government and the Yemeni government conspired to lie about the
incident, saying that the Yemeni government had launched the attack
rather than the U.S., and that the victims were members of an al-Qaeda
training camp.
After
exposing what really happened in the missle strike, Shaye was arrested
on apparently trumped-up charges and given a sham trial that was
criticized by major human rights organizations such as Amnesty
International and sentenced to five years in prison.
According to Amnesty International,
the unexploded cluster bomblet in the photo below was found at the
location of the missile strike in Yemen. It would have been one of the
166 bomblets carried by the Tomahawk cruise missile.
Each bomblet explodes “into
over 200 sharp steel fragments that can cause injuries up to 150m away.
An incendiary material inside the bomblet also spreads fragments of
burning zirconium designed to set fire to nearby flammable objects.”
To review:
In an incident which barely registered on the radar of the news media
and the American public, the U.S. government killed a bunch of women and
children. Then they lied about it to cover it up. Then, when they got
caught lying about it, they arranged to have the journalist who exposed
all the killing and lying kept in prison for reporting it.
If
you think that a government which routinely does that kind of stuff
(without any negative career consequences or political consequences or
legal consequences for those involved) – and which was previously caught
waging an illegal counterintelligence program against its own citizens –
could not possibly be acquiescing in an illegal program of organized
surveillance and harassment of targeted citizens, then you’re not skeptical – you’re just naïve.
________________________________________________________
4. Current Oversight of Law Enforcement and Intelligence Agencies
U.S.
law enforcement and intelligence agencies currently operate with
essentially the same cloak of secrecy that existed during the days of
Cointelpro and MK Ultra.
Following
the Church Committee investigations in the 1970s efforts were made to
implement policies to protect Americans from crimes by the federal
government. Unfortunately, those protections have been thoroughly undone
– especially by policies such as the Patriot Act enacted in the wake of
the 9/11 attacks. The FBI – and even the IRS – now assert the right to
have warrantless access to the email communication of all Americans, to
cite just one example.
Arguably,
even the Church Committee reforms aimed at outlawing assassinations of
foreign leaders have been undermined. The government now orders drone
assassinations in places like Yemen and launches wars without the
approval of Congress – such as the “military intervention” against Libya
launched in March 2011.
It’s
difficult to even assess the extent to which America’s law enforcement
and intelligence agencies have returned to being rogue entities, given
that they now routinely invoke “national security” as a justification
for keeping American citizens from knowing their business. Political
cowardice by members of Congress – as well as laziness, group-think, and
careerism among many journalists at major news outlets has resulted in a
lack of oversight of America’s most secretive government agencies.
Fortunately,
there are some exceptions; some journalists do report that the
intelligence and law enforcement communities have slipped the leash.
A Forbes magazine writer – to cite just one example – has suggested that we probably need another Church Committee investigation. The
Forbes article quotes a former senior NSA official, William H. Binney, who said we seem to be headed “toward an Orwellian state.”
A November 2013
article in the New York Times on
spying by the NSA quoted Binney on the danger of the intelligence
community’s powers being used as a weapon against Americans:
Mr.
Binney said that without new leadership, new laws and top-to-bottom
reform, the agency will represent a threat of “turnkey totalitarianism” —
the capability to turn its awesome power, now directed mainly against
other countries, on the American public. “I think it’s already starting
to happen,” he said. “That’s what we have to stop.”
Here
is another one of many examples of media coverage (not just crazy
blogger rants) about the creepy government surveillance of American
citizens.
This Mother Jones article describes the FBI’s “massive network of spies.”
In
light of all the above, the government’s acquiescence in organized
stalking hardly seems far-fetched. As America deteriorates toward an
increasingly Orwellian state, gang stalking victims are the canaries in
the coal mine.
________________________________________________________
5. Published Articles & TV Reports on Organized Stalking & Current Counterintelligence Operations
Depending
on how you arrived at this website, you might be partly familiar with
claims about organized stalking, but skeptical that it is widespread (or
even that it exists at all). I respect your skepticism.
If
you want to review some of the published articles on the subject before
delving into the historical and theoretical discussion presented in
this overview, you can go directly to such articles posted on this
website (with commentary and links) before proceeding.
Here are some examples:
An episode of the PBS News show NOW broadcast in
March 2004,
which addressed the issue of the possible re-emergence of the FBI’s
Cointelpro operations. NOW is an Emmy-winning weekly TV newsmagazine on
PBS. Tom Brokaw described NOW as “fearless about challenging
conventional wisdom.” The Austin American-Statesman called NOW ”one of
the last bastions of serious journalism on TV.”
While the video of the program is not posted on the PBS website, there is a synopsis of the show under the title “Cointelpro Again?”
Here is the relevant passage:
“Some
fear that something like COINTELPRO may again be at hand. There are
undercover agents infiltrating peaceful protests in America. Pretending
to be political activists, local law enforcement officials are
monitoring the activities of advocacy and protest groups based on what
one judge calls those organizations’ “political philosophies and conduct
protected under the First Amendment.” The tactic has come about as a
result of the relaxation of guidelines first put into place after the
COINTELPRO scandal investigation.”
An article in Newsweek in
June 2004 about
the Pentagon quietly re-entering the business of domestic spying. One
of the scandals (along with Watergate, Cointelpro, and other crimes)
which led to the U.S. Senate’s Church Committee investigations during
the 1970s was the spying on Americans by U.S. Army intelligence agents.
In the years following the 9/11 attacks, as this article noted, the
military sneaked back into that role:
“Without
any public hearing or debate, NEWSWEEK has learned, Defense officials
recently slipped a provision into a bill before Congress that could
vastly expand the Pentagon’s ability to gather intelligence inside the United States, including recruiting citizens as informants.”
An article in The Sunday Times, a major newspaper in the U.K., reported in October 2004 that the intelligence agency MI5 uses gang stalking tactics to punish whistle-blowers. In the article the tactics are referred to as
“zersetzung” – as the process was called by the Stasi (the state police of communist East Germany).
An article in The Globe and Mail, a Canadian national newspaper, which reported in
May 2006 that
the Canadian Security Intelligence Service (CSIS) and the Royal
Canadian Mounted Police (RCMP) used gang stalking techniques (referred
to as
“Diffuse and Disrupt” tactics) against terrorism suspects for whom they lacked sufficient evidence to prosecute.
An academic peer-reviewed criminology study of gang stalking in Belgium was published in the July–September 2006 edition of Revue Internationale de Criminologie et de Police technique et scientifique(volume
49), pages 350-373. Criminologist Nicolas Desurmont described how a
secret policy of criminal stalking sanctioned by law enforcement
authorities is used as an extrajudicial counterintelligence weapon to
psychologically terrorize targeted individuals. Desurmont has published
additional papers on the subject since then, and presented his findings
at international conferences on criminology. As of December 2013, no
(official) English translations of his papers were available (I
confirmed this with Mr. Desurmont), although the English language pdf
file linked below appears to be a competent translation – especially for
someone translating an academic text into a non-native language.
Vers une problématique du harcèlement criminel en réseau (2006)
The original document:
An English translation:
La geocriminologie en contexte de gang-stalking (2009)
Essai
de caractérisation des phénomènes de stalking dans un contexte
juridique et politique : radiogoniométrie et filature (2010)
A newspaper article in the Verona-Cedar Grove Times in
March 2009 titled
“Stalker Claims Unsettle Police” described how a self-proclaimed target
of gang stalking had been distributing flyers in his former
neighborhood in Verona, New Jersey, warning about organized stalking of
targeted individuals. The flyers stated:
“Their intention is to murder their target without getting their hands dirty. It’s the perfect hate crime.”
A post on the political blog Daily Kos in
October 2010 alleged that intelligence agencies in the U.S., the U.K., and Canada use gang stalking (
zersetzung as
East Germany’s Stasi called it) against targeted individuals. Although
the article did not provide sourced details, it might have helped raise
awareness of this form of state-sponsored criminal harassment since
Daily Kos receives several hundred thousand visits per day.
A local TV news broadcast in California in January 2011 (on
KION – Channel 46 and KCBA – Channel 35) featured a report about gang
stalking – referred to as such by the reporters and by Lieutenant Larry
Richard of the Santa Cruz Police Department.
An article in the Sun Sentinel, a Pulitzer Prize-winning newspaper in Florida, in
December 2012 about
the organized stalking of a police officer by other police officers and
sheriff’s deputies from multiple jurisdictions. The victim of the
stalking had cited an off-duty police officer for reckless driving (he
was later fired). The stalking – which included illegaly snooping on the
victim’s private data and efforts to harass and intimidate her – was
apparently done in retaliation. The
Sun Sentinal later won a
Pulitzer Prize for public service journalism for its series of articles
on deaths and injuries caused by reckless driving by Florida police
officers.
An article in CounterPunch magazine in
January 2013 which asserted that the FBI’s infamous Cointelpro operations have re-emerged in full force:
“Cointelpro is alive and well.”
An article in the Nation (America’s oldest continuously-published weekly magazine) in
June 2013 (
“The Strange Case of Barrett Brown”)
by Northwestern University professor Peter Ludlow, in which he stated –
in reference to actions by private security firms, the FBI, and the
Department of Justice:
“One might think that what we are looking at is Cointelpro 2.0 – an outsourced surveillance state – but in fact it’s worse.”
An article in the Washington Times and
an article in Wiredmagazine both discussed the widespread speculation that the
September 2013 mass
shooting at the Washington D.C. Navy Yard resulted from the shooter
having been systematically tormented by gang stalkers using electronic
weapons and noise harassment.
The cover article of Fortean Times in
October 2013 (U.S. edition) is about
“state-sponsored gangstalking.” The
magazine is a U.K.-based publication about odd news. The author, a
professor from California State University Long Beach, describes in
detail how a former military service member who stole some equipment
from the U.S. military has been relentlessly stalked by undercover
operatives and tortured using psychological operations tactics and
electronic weapons.
A local TV news broadcast in West Virginia on 14
November 2013(on
WDTV – local CBS News affiliate Channel 5) presented a report about
“organized stalking.” The broadcast featured testimony by two
individuals from Pennsylvania who appear to be credible and sincere,
discussing their constant harassment by perpetrators using gang stalking
tactics.
A TV and radio broadcast of Democracy Now! on 25
November 2013 featured
an interview with Gary Ruskin, director of the Center for Corporate
Policy in which he discussed the shadowy industry of spies employed by
major U.S. corporations to conduct secret – and often illegal –
counterintelligence operations against critics of those corporations.
Articles published by CBS, the Daily Mail, RT, Tech Dirt, and Courthouse News Service in
December 2013 reported
that a U.S. government contractor filed a lawsuit against multiple
federal agencies for gang stalking him (the complaint refers to gang
stalking as such). The plaintiff claimed that his stalking began after
he made a Google search for information about how to build a
radio-controlled airplane. While typing his query, Google’s
auto-complete function finished his
“How to build a radio-controlled…” query with the word
“bomb.” The
individual was then subjected to constant surveillance – including
inside his residence and his vehicle – and constant psychological
harassment from co-workers and strangers.
________________________________________________________
6. Historical Predecessors of Gang Stalking: Cointelpro, MK Ultra, Red Squads, & Stasi
J. Edgar Hoover
If
I were creating an education plan for American high school students, I
would require that everyone take a class during his or her senior year
that reviewed the major conspiracies and scandals of American
government: the Teapot Dome scandal, the Pentagon Papers, Watergate,
Iran-Contra, etc. No one can participate intelligently in a democracy
without such an historical background.
Gang
stalking is the U.S. government’s current incarnation of the tactics
and strategies employed by previous secret illegal federal programs,
such as the FBI’s Cointelpro (“Counter-intelligence Program”) and the CIA’s Project MK Ultra.
Anyone
who doubts that the U.S. government would be currently sanctioning a
widespread conspiracy involving illegal surveillance and harassment of
targeted American citizens should read the basic facts about those two
programs. Don’t even bother with obscure sources of information; simply
read the established mainstream accounts of the undisputed facts. The
details are deeply disturbing.
**************************************************
Cointelpro
Cointelpro was
a secret illegal program in which U.S. law enforcement personnel and
their various government and private citizen accomplices systematically
spied on, slandered, terrorized, and committed acts of violence
(including murder) against American citizens. The program ended after
being exposed in 1971 by civilian activists who obtained information
about it and leaked it to the news media.
It
would be difficult to overstate the relevance of the Cointelpro
operations to modern gang stalking in the U.S. By all available
evidence, current organized stalking crimes in the U.S. are not similarto Cointelpro; they are a continuation of Cointelpro.
Significantly,
Cointelpro was not exposed by insider whistle-blowers; the FBI agents
and their civilian minions dutifully perpetrated their assigned crimes
until the operations were derailed by civilian outsiders.
Exposure
of the program required those civilians to break into an FBI office and
steal documents about the program and give them to the news media.
Also bear in mind: J. Edgar Hoover’s name is still on the FBI headquarters building.
As noted in the introduction above,
a January 21, 2013 article inCounterPunch magazine asserted
that Cointelpro is now secretly being used again on a wide scale. In
that article, “The Return of Cointelpro?” Tom McNamara describes the
original program – and its re-emergence – as follows:
For
15 years (1956-1971) the Federal Bureau of Investigation (FBI) ran a
broad and highly coordinated domestic intelligence / counterintelligence
program known as COINTELPRO (COunter INTELligence PROgrams). What was
originally deemed as a justifiable effort to protect the US during the
Cold War from Soviet and Communist threats and infiltration, soon
devolved into a program for suppressing domestic dissent and spying on
American citizens. Approximately 20,000 people were investigated by the
FBI based only on their political views and beliefs. Most were never
suspected of having committed any crime.
The
reasoning behind the program, as detailed in a 1976 Senate report, was
that the FBI had “the duty to do whatever is necessary to combat
perceived threats to the existing social and political order.” The fact
that the “perceived threats” were usually American citizens engaging in
constitutionally protected behaviour was apparently overlooked. The
stated goal of COINTELPRO was to “expose, disrupt, misdirect, discredit,
or otherwise neutralize” any individual or group deemed to be
subversive or a threat to the established power structure.
The
FBI’s techniques were often extreme, with the agency being complicit in
the murder and assassination of political dissidents, or having people
sent away to prison for life. Some of the more “moderate” actions that
were used were blackmail, spreading false rumors, intimidation and
harassment. It has been argued that the US is unique in that it is the
only Western industrialized democracy to have engaged in such a wide
spread and well organized domestic surveillance program. It finally came
to an end in 1971 when it was threatened with public exposure.
Or did it?
In
a stunning revelation from the Partnership for Civil Justice Fund
(PCJF), it appears that COINTELPRO is alive and well. Through a Freedom
of Information Act (FOIA) request, PCJF was able to obtain documents
showing how the FBI was treating the Occupy Wall Street (OWS) movement,
from its inception, as a potential criminal and domestic terrorist
threat.
The
article doesn’t mention the phrase “gang stalking,” but if you don’t
see the connection, you’re in over your head. If you’re a journalist or a
politician, this is probably as close as you will get to a memo telling
you to wake up and grasp what is happening.
The
author, Tom McNamara, provides an excellent review of the original
program, and an analysis of its current incarnation. You can judge for
yourself whether he feels free to discuss such things because he’s on
the other side of the Atlantic Ocean.
McNamara is “an Assistant Professor
at the ESC Rennes School of Business, France, and a Visiting Lecturer
at the French National Military Academy at Saint-Cyr, Coëtquidan,
France.”
Retired FBI Official from Cointelpro Era Tried to Expose Modern Gang Stalking
Among
the most compelling testimony about the current widespread existence of
gang stalking is that of a man who was familiar with Cointelpro
operations because he participated in them as an FBI official.
The late Ted L. Gunderson served
as the head of the FBI field offices in Los Angeles, Dallas, and
Memphis. After retiring from the FBI in 1979, he became a private
investigator. His investigations included working for the defense in the
famous murder case involving former U.S. Army physician, Dr. Jeffrey
MacDonald.
In
a series of public appearances (and in an affidavit linked below)
Gunderson revealed that “rogue” military intelligence and law
enforcement units of the federal government oversee a nationwide network
of community-based gang stalkers who monitor, harass, and intimidate
thousands of American citizens who have been extrajudicially targeted as
dissidents or undesirables.
Gunderson
claimed that his efforts to expose gang stalking resulted in him
becoming a victim himself, as efforts were made to silence him.
Here is an audio clip from
a presentation Gunderson gave in which he described how organized
stalking tactics – such as electronic surveillance and “gas lighting” –
were used against him.
According
to Gunderson, gang stalking has been operational since the early 1980s
(i.e., it began only a few years after the U.S. Senate thought they had
pulled the plug on Cointelpro following the Church Committee
investigations). Gunderson said that the scope, intensity, and
sophistication of gang stalking have increased since its inception, as
it exploits new surveillance and communication technologies.
Analysis
of Ted Gunderson’s claims about gang stalking is complicated for
several reasons. On one hand, he was a former high-level FBI official
who worked in the agency during the era of Cointelpro, so he had
professional expertise and first-hand experience with that agency’s
counterintelligence operations. On the other hand, his public statements
about gang stalking – for example in his affidavit which you can view
below, as well as his public discussions of the matter (which can be
found on YouTube) include references to various fringe topics, such as
satanism and child sex rings, and such.
Such
references – along with the fact that he is no longer around to clarify
or defend his claims – raise several questions that might never be
answered. History contains many examples of well-documented serious
crimes, bizarre human experiments, and odd beliefs by sociopaths at high
levels of government (in the U.S. and other nations), but Gunderson
never proved his theories.
At
the same time, anyone skeptical of Gunderson’s claim about the U.S.
government’s complicity in gang stalking must admit that he cannot be
easily dismissed. If he was crazy – or an incompetent investigator – how
come no one noticed that when he was in charge of the FBI’s Los Angeles
field office?
__________________________
FBI’s Gang Stalking Campaign Against Actress Jean Seberg
For
a sense of the evil nature of gang stalking, take a look at one of the
most high-profile well-documented cases of it perpetrated by the FBI in
the days of the original Cointelpro operations.
My November 23, 2013 post on
the “Gang Stalking News” page of this website is on a documentary about
the well-known film actress, Jean Seberg, who was systematically
terrorized by the FBI for her support of the civil rights movement.
This
was a case with explicitly incriminating “smoking gun” FBI memos and
mainstream news reports documenting what the feds did to their victim.
(Those documents are included in my post.)
FBI
agents blacklisted Seberg, slandered her by planting false stories
about her in the news media, monitored her with covert surveillance
(wiretaps), and terrorized her with overt surveillance (stalking) and
black bag jobs (break-ins).
Emotional
distress from the FBI’s operations against Ms. Seberg – while she was
pregnant – apparently caused her to give birth prematurely (her baby
died), and ultimately led her to commit suicide. Ms. Seberg was just one
of many victims targeted by the FBI’s secret police program.
__________________________
The Break-in
A fascinating but under-reported aspect of Cointelpro is the break-in which led to the program’s exposure.
THIRTY-FIVE
YEARS ago today, a group of anonymous activists broke into the small,
two-man office of the Federal Bureau of Investigation in Media, Pa., and
stole more than 1,000 FBI documents that revealed years of systematic
wiretapping, infiltration and media manipulation designed to suppress
dissent.
The
Citizens’ Commission to Investigate the FBI, as the group called
itself, forced its way in at night with a crowbar while much of the
country was watching the Muhammad Ali-Joe Frazier fight. When agents
arrived for work the next morning, they found the file cabinets
virtually emptied.
Within
a few weeks, the documents began to show up — mailed anonymously in
manila envelopes with no return address — in the newsrooms of major
American newspapers. When the Washington Post received copies, Atty.
Gen. John N. Mitchell asked Executive Editor Ben Bradlee not to publish
them because disclosure, he said, could “endanger the lives” of people
involved in investigations on behalf of the United States.
Nevertheless,
the Post broke the first story on March 24, 1971, after receiving an
envelope with 14 FBI documents detailing how the bureau had enlisted a
local police chief, letter carriers and a switchboard operator at
Swarthmore College to spy on campus and black activist groups in the
Philadelphia area.
More
documents went to other reporters — Tom Wicker received copies at his
New York Times office; so did reporters at the Los Angeles Times — and
to politicians including Sen. George McGovern of South Dakota and Rep.
Parren J. Mitchell of Maryland.
To
this day, no individual has claimed responsibility for the break-in.
The FBI, after building up a six-year, 33,000-page file on the case,
couldn’t solve it. But it remains one of the most lastingly
consequential (although underemphasized) watersheds of political
awareness in recent American history…
Update….
_________________________
The Official Reports
Since
the FBI committed so many crimes against Americans during this era,
there are thousands of pages of documents in the U.S. Senate’s Church
Committee reports.
Most
Congressional reports are boring – but not these. Among the most
interesting documents (and the most relevant to gang stalking) are the
three which you can view or download below.
Just browsing through the contents pages gives a sense of the scope of the FBI’s crimes. Here are some of the topic headings:
Use of illegal or improper means, mail opening, political abuse,ignoring the law, efforts to discredit, media manipulation, distorting data to influence government policy and public perception,Congress declines to confront the issue “infiltration” investigations, wiretaps,bugging, FBI political intelligence for the White House, exaggeration of communist influence, “Black Bag”jobs, misuse of the IRS by the FBI and CIA, targeting of ideological groups, NSA monitoring, warrantless electronic surveillance, domestic intelligence network, violent and illegal activities of informants, targeting law-abiding citizens, targeting critics and political figures, attorneys general failure to limit and control FBI intelligence activities, efforts to promote enmity and factionalism within groups or between groups, encouraging violence between groups, efforts to prevent speaking/teaching/writing and publishing, propaganda, fictitious organizations, disseminating derogatory information to family, friends, and associates, contacts with employers, interference with the judicial process, blurred distinction between counterintelligence and investigation.
These
reports are filled with interesting stuff. For example, Volume 6 of the
hearings contains, among other items, a letter about “black bag jobs”
(referred to as such). Book 2 of the final reports refers to an apparent
attempt to blackmail Martin Luther King, Jr. and encourage him to
commit suicide (pages 220-221).
This U.S. Senate webpage has all the Church Committee reports:
_________________________
Two
of the individuals deemed “subversives” by the FBI and targeted under
the original Cointelpro: Martin Luther King, Jr. and John Lennon.
**************************************************
MK Ultra
Project
MK Ultra was a secret illegal program run by the CIA in which mind
control and torture experiments were performed on U.S. and Canadian
citizens from the early 1950s until the early 1970s.
Many
experiments were performed without the consent of the subjects – and in
some cases without the subjects even being aware that they were being
used for experimentation.
The
mind control and torture methods that were tested included sensory
deprivation, isolation, hypnosis, verbal and sexual abuse, and the
administration of drugs and substances which caused confusion, brain
damage, blistering, and paralysis.
That might explain why there are no MK Ultra tribute floats in America’s various holiday parades.
The
experiments were performed at dozens of colleges and universities,
hospitals, prisons, and pharmaceutical companies in the U.S. and Canada.
Front organizations were used by the CIA to operate the program through
those institutions, although in some cases the top officials at the
institutions knew about the CIA’s involvement.
Keep
that in mind when you evaluate the plausibility that a widespread
program of organized stalking could exist without being compromised by
various officials at private and public institutions and organizations.
In
the mid-1970s the program was exposed by the U.S. Senate’s Church
Committee investigations. Those investigations (which also examined
Cointelpro) were a response to a series of revelations about crimes by
the U.S. government, including the attempted assassinations of foreign
leaders, the U.S. Army’s spying on civilians, Cointelpro, and the
Watergate scandal.
In
1973, when MK Ultra was being exposed, CIA Director Richard Helms
destroyed most of the records associated with the program to ensure the
American public would never learn the full scope of the agency’s crimes.
One of the best books on the subject is
The Search for the “Manchurian Candidate” by
John D. Marks. The award-winning book was highly-praised by Seymour
Hersh – the famous investigative journalist who exposed the My Lai
Massacre and Nixon’s secret bombing of Cambodia during the Vietnam war.
Another widely-praised book on MK Ultra is
Operation Mind Control by
Walter Bowart. It was originally published in 1978. An updated and
expanded (“researcher’s edition”) published in 1994 can be downloaded as
a pdf
at this website.
**************************************************
Red Squads
Red
Squads are another historical predecessor of gang stalking in the U.S.
They were counterintelligence units within police departments in large
cities, and pre-dated the creation of the FBI.
A Wikipedia description:
“Red
Squads were police intelligence units that specialized in infiltrating,
conducting counter-measures and gathering intelligence on political and
social groups during the 20th century. Dating as far back as the
Haymarket Riot in 1886, Red Squads became common in larger cities such
as Chicago, New York, and Los Angeles during the First Red Scare of the
1920s. They were set up as specialized units of city police departments,
as a weapon against labor unions, communists, anarchists, and other
dissidents.”
For a well-researched account of Red Squads, see the book
Protectors of Privilege (published in 1990) by Frank Donner, a civil rights lawyer.
As
the title of Donner’s book suggests, Red Squads and private
investigators played the same role in their day as today’s FBI and
private intelligence-security contractors. The current federal law
enforcement community was described by Anonymous hacker-activist Jeremy
Hammond (now serving a 10-year prison sentence) as “the boot boys of the 1 percent, paid to protect the rich and powerful.”
Here
is Frank Donner’s description (page 12) of the role of law enforcement
personnel and private intelligence contractors in Chicago during the
1880s:
“The
reliance by the Chicago business community on repressive police tactics
to deal with labor unrest was unconcealed. Indeed, the Chicago police
were as much the minions of the business community as hired Pinkertons.”
**************************************************
The Stasi
Insignia of East Germany’s “Ministry for State Security”
Communist East Germany’s Stasi – its secret police agency – is another historical predecessor of gang stalking.
The psychological terrorism strategies used by the Stasi were referred to as “zersetzung” –
which translates as “decomposition” or “corrosion.” As used to refer to
the Stasi’s tactics, the term meant “to undermine or subvert.” Zersetzung is the noun; zersetzen is the verb.
Methods
used by the Stasi – which included overt and covert surveillance,
slander, and psychological operations (“psyops”) tactics –
were essentially identical to those currently used in organized stalking
in counterintelligence operations in America and elsewhere.
Gang
stalking harassment tactics described later in this overview borrow
heavily from the psychological torture methods refined by the Stasi.
Arguably,
the activities of the Stasi are even more closely relevant to modern
gang stalking in the U.S. than Cointelpro. The Stasi was famous for
controlling citizens by seeding East German society with spies. A
January 18, 2008 article in Wired magazine described it this way:
“As the enforcement arm
of the German Democratic Republic’s Communist Party, the Stasi at its
height in 1989 employed 91,000 people to watch a country of 16.4
million. A sprawling bureaucracy almost three times the size of Hitler’s
Gestapo was spying on a population a quarter that of Nazi Germany.
Unlike
the prison camps of the Gestapo or the summary executions of the Soviet
Union’s KGB, the Stasi strove for subtlety. “They offered incentives,
made it clear people should cooperate, recruited informal helpers to
infiltrate the entire society,” says Konrad Jarausch, a historian at the
University of North Carolina at Chapel Hill. “They beat people up less
often, sure, but they psychologically trampled people. Which is worse
depends on what you prefer.”
That finesse helped the Stasi quell dissent, but it also fostered a pervasive and justified paranoia.”
Here is the interrogation center where the psychological torture methods of zersetzung were refined. These are the isolation cells in the Hohenschoenhausen Prison in Berlin – which is now a museum.
Click on image to enlarge.
The following excerpt from a Wikipedia entry on the Stasi provides a good description of their strategy and tactics:
By
the 1970s, the Stasi had decided that methods of overt persecution
which had been employed up to that time, such as arrest and torture,
were too crude and obvious. It was realised that psychological
harassment was far less likely to be recognised for what it was, so its
victims, and their supporters, were less likely to be provoked into
active resistance, given that they would often not be aware of the
source of their problems, or even its exact nature. Zersetzung was
designed to side-track and “switch off” perceived enemies so that they
would lose the will to continue any “inappropriate” activities.
Tactics
employed under Zersetzung generally involved the disruption of the
victim’s private or family life. This often included psychological
attacks such as breaking into homes and messing with the contents –
moving furniture, altering the timing of an alarm, removing pictures
from walls or replacing one variety of tea with another. Other practices
included property damage, sabotage of cars, purposely incorrect medical
treatment, smear campaigns including sending falsified compromising photos or documents to the victim’s family, denunciation, provocation, psychological warfare, psychological subversion, wiretapping, bugging, mysterious phone calls or unnecessary deliveries, even including sending a vibrator to
a target’s wife. Usually victims had no idea the Stasi were
responsible. Many thought they were losing their minds, and mental
breakdowns and suicide could result.
One
great advantage of the harassment perpetrated under Zersetzung was that
its subtle nature meant that it was able to be denied. That was
important given that the GDR was trying to improve its international standing during the 1970s and 80s.
Zersetzung techniques have since been adopted by other security agencies, particularly the Russian Federal Security Service (FSB).
For
more information on the psychological torture methods used by the Stasi
– and still used today by the FBI, the CIA, and their minions – you
can visit
this website.
A film about the Stasi - “The Lives of Others” (“Das Leben der Anderen” was the German title) – won the Academy Award for Best Foreign Language Film (2006).
__________________________________________________________
7. The National and International Scope of Gang Stalking
Well-documented
historical and contemporary reporting makes it abundantly clear that
organized stalking tactics have been – and continue to be – used by
various foreign intelligence services and law enforcement agencies. In
the section below, for example, is a news report about a first-hand
account of organized stalking tactics being used by Russian intelligence
agents. No one disputes that such tactics were widely used by East
Germany’s Stasi.
Two
mainstream news articles I posted in the “Gang Stalking News” section
of this website (October 10, 2004 and May 31, 2006) are about gang
stalking tactics used by intelligence and law enforcement agencies in
Northern Ireland and Canada.
Incidentally,
the U.S. Senate Church Committee investigations found that the
government of Canada was also complicit in the infamous CIA program, MK
Ultra.
Peer-reviewed
academic research articles published by criminologist Nicolas Desurmont
(see the “Published Articles” section of this overview above) show that
gang stalking has been used extensively by law enforcement agencies in
Belgium.
From
my perspective, another indication of the international scope of gang
stalking is the Internet traffic and emails to this website from
countries all over the world.
Based
on personal experience and numerous accounts by self-proclaimed
victims, organized stalking occurs across the nation here in the U.S.
Apparently, moving from one area to another is not likely to help a
victim avoid being stalked. Similarly, international cooperation among
law enforcement and intelligence agencies means that moving from the
U.S. to Canada is probably not going to be helpful.
The most realistic solution is to expose the criminal activities of intelligence and law enforcement agencies – and their private contractors – to the public.
__________________________________________________________
8. Investigation, Surveillance, and Harassment Tactics
Investigation
Apparently, gang stalking begins with a deep investigation of the targeted individual.
An investigation serves multiple purposes in counterintelligence:
(1)
Information gathered about the target can later be used to tailor the
surveillance and harassment (subversion) strategies. In some cases, an
investigation could also reveal that the target is unsuitable for gang
stalking because he or she has connections and resources which would
enable the target to fight back.
(2)
In the unlikely event that acts of harassment get exposed, formal
documentation that an “investigation” was being performed could possibly
be cited to explain some of the suspicious activity (for example, overt
stalking could be easily explained as “covert surveillance” that
happened to be noticed by the target).
(3)
Law enforcement and intelligence personnel – public and private – at
various levels are sometimes under pressure to show that they are being
productive, so there could well be a de facto quota for conducting
investigations of “suspicious” persons.
(4)
Acts of subversion can be seamlessly incorporated into what is
ostensibly an investigation. As noted above, overt stalking is a prime
example. Stalking was one of the tactics used by the FBI in their
subversion campaign against the actress Jean Seberg during their
Cointelpro operations, for example. (After years of such harassment she
committed suicide.) Another tactic – also used during Cointelpro against
various targeted individuals – was slander. An investigation provides a
legally bullet-proof opportunity to slander the victim. If an
investigator quietly begins questioning persons associated with a
targeted individual (co-workers, friends, etc.), and tells them that he
is conducting an investigation, it could easily destroy the target’s
reputation and relationships.
Obtaining
information from the targeted individual and from persons who know the
targeted individual is a process undercover investigators and spies call
“elicitation.” This pdf document from the FBI explains the strategies
and tactics of elicitation:
FBI Elicitation Tactics
Surveillance
As
with investigations, the surveillance element of organized stalking
involves the same tactics used around the world by many private
investigators, intelligence agents, and law enforcement personnel: black
bag jobs, electronic surveillance (phone wiretaps, hacking of personal
computers, listening devices, spy cameras, GPS-monitoring of vehicle
location, etc.), combined with direct visual surveillance (“human
intelligence”) by various accomplices.
Most
personnel involved in managing and performing organized stalking are
paid for their services – whether they work directly for an agency such
as the FBI, or for private intelligence-security contractor firms, or as
criminal “informants.” Others though, are recruited to assist as
volunteers. For example, when the FBI’s illegal Cointelpro operations
were exposed, internal documents showed that the agency had enlisted a
local police chief, letter carriers, and a switchboard operator at
Swarthmore College to spy on campus and black activist groups in the
Philadelphia area.
Harassment Tactics (“Subversion”)
In
counterintelligence, to “subvert” or “neutralize” an enemy is to make
it impossible for that enemy to go about his business. Gang stalkers
seek to keep their victim in a constant state of agitation and
hyper-vigilance so that he or she will find it almost impossible to
function.
This
serves multiple purposes. For one thing, it makes it hard for the
individual to pose a threat to the client of the gang stalkers – whether
that is a corporation or a government.
Note
that – as discussed in detail elsewhere in this website – the
distinction between corporations and the government is often meaningless
in America, given the vast industry of private intelligence contractors
with secret clearances, the use of the FBI and other agencies to serve
corporate interests, and the lucrative revolving-door nature of
employment between the public and private spheres in law enforcement and
intelligence. This is another obvious purpose of gang stalking: income
for the perpetrators.
Another
function of gang stalking is to exact revenge against the victim.
Stalking is a form of extra-judical punishment for anyone who crosses
someone with connections to the vast homeland security infrastructure.
Constant
surveillance of targeted individuals (described above) is also an
element of subversion. Anyone who knows that he or she is under constant
surveillance will not only be inhibited from acting against the
interests of the client of the gang stalkers, he or she will also find
it difficult to fight back against the harassment or evade the
surveillance itself because many efforts at counter-measures will be
observed by the stalkers. In addition, anyone who is aware that he or
she is constantly being watched by illegal spying will suffer the
emotional trauma caused by having virtually no privacy.
“Harassment”
is an appropriate description of many of the individual acts
perpetrated against gang stalking victims since they are intended to
annoy, anger, and frustrate the targeted individual – rather than, say,
physically injure him or her. On the other hand, “harassment” does not
begin to convey the severity of the cumulative psychological effects of
organized stalking.
Slander,
verbal abuse, noise, threats by strangers, constant surveillance, and
other tactics, performed daily over a period of years will cause
psychological torture, social isolation, and financial destruction.
According to some anonymous sources, the overall process is sometimes called “slow kill.” Regardless
of whether that term is actually used by perperators of gang stalking,
it is an appropriate description. East Germany’s Stasi (state police)
referred to it as“zersetzen” – to corrode or decompose.
Some
of the psychological operations tactics described below have ancient
roots; the frequent and sustained use of noise to torment enemies, for
example dates back to ancient siege warfare, and is still used in
military operations – such as the U.S. invasion of Panama in 1989.
For
the most part, tactics are chosen for their lack of directly observable
and legally persuasive evidence. The idea is to completely destroy
someone without leaving fingerprints.
Intelligence-gathering
and policing are often done in ways that make it inherently difficult
to prove misconduct. Gang stalking employs a refined set of practices
specifically chosen for the lack of legally incriminating evidence, and
for the likelihood that victims’ accounts will be perceived as simply
paranoid impressions of routine events when described to others.
Victims’
accounts tend to be dismissed since their experiences sound like
commonplace occurrences – because that is indeed what they are:
strangers who are rude, noisy neighbors, bad service, being cut-off in
traffic, etc. These are things which happen to everyone. But for gang
stalking victims, these things happen constantly – which becomes a form of real psychological torture, which must be experienced to comprehend.
Below
are the primary tactics associated with counterintelligence
subversion. Keep in mind that, by all accounts, a gang stalking campaign
starts employing these tactics long before the victim has any clue that
he or she is being systematically targeted. Many of the early instances
of harassment are only understood by the victim later when the whole
process becomes clear. By that point, often the harassment and
slandering might have been going on for years.
Slander
As
mentioned above, an investigation – or even the pretense of an
investigation – is a perfect opportunity to slander a target. If someone
who even appears to be an investigator or undercover cop begins quietly
asking neighbors, employers, relatives, and co-workers about a targeted
individual, it will almost certainly begin to corrode that person’s
reputation, even if no explicit allegations are made.
Sometimes slander in a counterintelligence operation can be much more aggressive. A textbook example is
the FBI’s successful campaign to destroy the career and life of film actress Jean Seberg during
their Cointelpro operations. That case is noteworthy both because it
involved a high-profile target – Seberg was a successful actress in the
prime of her career – and also because internal FBI memos and news
reports explicitly revealed that they were deliberately spreading lies
about her.
Tactics
used in the spying-and-lying industry are unfamiliar to the general
public. Many people will assume that anyone posing as an “investigator”
is legitimate. If you doubt that, watch the
video clip of the ABC program in
the “Gang Stalking Videos” page of this website regarding how easily
civilians can be recruited to assist in crimes against strangers – such
as in gang stalking operations.
Blacklisting
A
tactic closely related to slander is blacklisting. For centuries
blacklists have been used to identify and discriminate against
individuals (and organizations) deemed to be undesirable. In U.S.
history the most famous example was the blacklisting of leftists in the
entertainment industry during the 1940s and 1950s.
The
tactic is perfectly suited to counterintelligence subversion because it
undermines the targeted individual in a way that will likely force the
victim to be preoccupied with economic survival rather than political
activism or whistle-blowing.
Mobbing
Newsweek magazine
published an article in August 2000 titled “They Call it Mobbing.” The
article (which you can see in the “Gang Stalking News” section of this
website) describes a process of intense systematic harassment of a
targeted employee by multiple co-workers and managers at his or her
workplace. The abuse involves slandering and isolating an employee and
verbal abuse. Apparently, this is a common element of gang stalking
campaigns against targeted individuals. Since the tactic is apparently
widespread – and since it is apparently connected in some cases to
workplace violence – I have devoted the entire next section to it in
this overview.
Black Bag Jobs
Breaking
into the residence or office of a target is another tactic common to
both gang stalking victims and targets of previous government
conspiracies such as Cointelpro and Watergate. Among the obvious motives
are to gather information, and to plant audio and video surveillance
devices.
As
noted in the section above about the FBI’s Cointelpro operations, the
Senate’s Church Committee reports contain an FBI letter about black bag
jobs – referred to as such – which makes clear that the agency had no
illusions about the fact that the tactic was completely illegal (just as
it is today).
Gas-Lighting
Another
example of a classic psyops tactic often reported by gang stalking
victims is “gas-lighting” – in which perpetrators enter the victim’s
residence and re-locate certain objects to make victims doubt their own
memory and create confusion – or to send a message that the victim’s
life has been invaded and is now under intense surveillance. Such
activities usually stop short of theft – which could lead to police
reports. If items are stolen, they are typically limited to items that
would be inexpensive and therefore unlikely objects of theft – so
reports of the incident will seem implausible and evidence of mental
instability.
In this short video clip, Luke Harding, a journalist with the Guardian, describes his personal experience with gas-lighting tactics being used against him by Russian intelligence agentswhile he was living in Moscow. I first saw this video on the “Gang Stalking is Murder” website.
Harding
naturally found the experience unsettling, but keep in mind that he had
the total support of his wife and his employer. Most victims of gang
stalking are more isolated and if they attempt to describe the
experience to others, are met with skepticism. The most likely reaction
is to assume that the victim simply forgot where he placed something, or
whether he left the window open, etc.
Abusive Phone Calls
As
with adolescent pranks, phone calls to the victim’s residence are an
easy way to harass the victim. Messages can range from insults to
threats, although they are subtle, not explicit, in case the calls are
being recorded.
Computer Hacking
Of
course, this is not unique to gang stalking victims: targets of
computer hacking range from random individuals to corporations and
governments. The practice can be done for surveillance or harassment or
both. See the first section in the “Tactics for Fighting Back” page of
this website for an example of how this was used against me.
Framing
As
with most of these gang stalking tactics, you can just use your
imagination regarding how this could work. Planting evidence can be done
either to further a slander campaign, or to actually set up the victim
for arrest and prosecution. Additionally, planting evidence can be
intentionally done in ways that the victim himself will easily find the
evidence – just to send the threatening message that target is
vulnerable to this type of attack.
Threats
Other
such threats are apparently common in gang stalking cases. They can
take any form imaginable, but will inevitably be anonymous and difficult
to prove. At one point, the gang stalking crew in my neighborhood began
dropping life insurance pamphlets on the walkway inside my courtyard.
Vandalism
Since
gang stalking victims are normally under virtually constant
surveillance, and since they are rarely in a position to afford
counter-surveillance measures to capture evidence of the harassment
being done, it’s easy to commit minor acts of vandalism against their
premises and belongings. This can be dumping trash on the lawn,
scratching the paint of their car, or whatever. Victims should not
assume that perpetrators are above doing physical harm to their pets
either; I know this both from personal experience and from accounts by a
few individuals I have reasons to regard as very credible.
Baiting
Baiting
is any effort to evoke a response by the victim which can be used to
discredit or legally ensnare him. In a sense, all gang stalking tactics
are forms of baiting because their cumulative effect will eventually
drive the victim to respond in ways that will create additional trouble.
Street Theater
A
commonly-reported tactic involves staging various actions by strangers
the victim encounters in public. Typically both the comments and actions
of the perpetrators will be carefully scripted to resonate with the
victim and to appear benign if captured on video or seen by witnesses.
Blocking/Cutting-Off/Invasion of Personal Space
One
example of gang stalking “street theater” is to cut-off the victim –
when he or she is walking, driving, or riding a bicycle. A related
tactic is to crowd the victim by rudely invading his or her space or
brushing against the person. Since this occasionally happens to everyone
in the normal course of events, accounts by the victim will likely
sound paranoid when described to others. Also, anyone nearby will be
unlikely to notice – let alone understand that the action was
deliberate.
This
tactic was described – among other places – in some information posted
in the late 1990s by a small group based in Canada called Spy & Counterspy –
whose website indicated that they wanted to reveal tactics used by
corrupt and repressive law enforcement agencies. This was part of the
group’s self-description:
“We are located just across the border in Canada (nine miles outside the reach of the FBI, BATF, DEA, and other goon squads).”
The
group – which claimed to have sources in the intelligence and law
enforcement industry – reported that the FBI uses a tactic called“managed aggression” when they are trying to apply pressure to the subject of a surveillance operation.
This is their description of this psychological operations tactic:
Here is an example of how an FBI surveillance team will deliberately provoke you.
When
you’re walking through a mall or a downtown shopping district, the
surveillance team will intentionally interfere with your route. A
pavement artist will “absent-mindedly” cross your path, forcing you to
change course to avoid walking into him. A group of agents will
“inadvertently” obstruct your path – they’ll be standing together
chatting, forcing you to walk around them. Other pavement artists will
“accidentally” create near-misses as you walk along. Some of these
“pedestrians” will create situations with a potential for a head-on
collision, forcing you to dodge them.
As
the psychological pressure continues to build, agents may “innocently”
bump into you, jostle you, or step on your heel from behind. A group of
pavement artists will cue up ahead of you, creating a line-up that
delays you as you try to make a purchase, order fast food, buy tickets,
and so on.
Activity
like this can quickly create frustration, even anger, in you. But
because the incidents occur in public locations, it’s difficult to prove
who’s behind them. You never see any agent more than once. You don’t
know where the next provocation is going to come from. You’re beginning
to get upset, irritated, unstable. You’re more likely to make mistakes
in judgment. And that’s exactly what the surveillance team wants.
As the authors also mentioned, the tactic’s effectiveness is much greater when it is unexpected:
This is a wicked mind-game. It can be very effective if you’re not anticipating it.
Targets
of gang stalking should expect this tactic and have a clear idea in
mind of how they will respond. Here is a good response to this tactic –
or for that matter, any type of street harassment by a “pavement
artist.”
Put
your cell phone to your ear as if you are on a phone call (if you don’t
have a cell phone immediately accessible, just put your hand to your
ear as if you were holding a cell phone – it doesn’t need to be
convincing), look directly at the perp’s face and smile and say – very loudly:
“They
sent a brown-noser! Can you hear me? Sorry, I have a bad cell phone
connection – I’ll try to talk loudly. I said: They sent a brown-noser!
Yeah, just some retard who will do anything he’s told. He doesn’t even
know who he’s working for. Just some brown-noser! I said: he’s just some brown-noser!”
Keep smiling and looking at the perp and wink at him. Message delivered.

Sensitization
As
described in some of the sections below, perpetrators of organized
stalking sometimes make use of various cutting-edge technologies, but
psychological torture does not require electronic hardware. Nor does it
even require unconventional psychology.
A
basic concept in Neuro-Linguistic Programming (NLP) is that a
particular stimulus – such as a sound or gesture – can become associated
or “anchored” in the thoughts and reactions of an individual through
repetition. Gang stalkers exploit this phenomenon by repeatedly
performing a particular action – such as generating a particular sound
as part of a noise harassment campaign.
Since
the victim is made aware that the sound is an element of the
harassment, his or her mind will naturally begin responding to that
sound as a “trigger” for a negative emotional reaction. It’s a way to
keep the victim constantly agitated because he or she will have the
negative response whenever stalkers generate the sound – or even when
the sound occurs in the normal course of events.
Synchronization
Similar
to sensitization, “synchronizing” is when gang stalking perp’s always
perform a particular action at the same moment as a particular action by
the victim. For example, whenever the victim leaves his residence, a
stalker in the area will cough or honk a horn or slam a door. It is a
way of reminding the targeted individual that he or she is under
constant surveillance.
Noise Harassment
One of the major weapons in the arsenal of gang stalkers is noise.
The
tactic is ancient; it has been used in siege warfare for centuries. If
you want to see a good dramatic portrayal of it, watch the final episode
of Season 2 of Game of Thrones, in which a horn was sounded constantly to break-down a character (Theon) in the castle Winterfell, which was under siege.
It
was widely reported that loud music was used by the U.S. military in
its invasion of Panama in 1989 to harass General Manuel Noriega and
flush him from the Vatican Embassy where he was holed-up. Accounts
differ about exactly how and why the tactic was used in that instance,
but no one questions the potential effectiveness of noise to create
distress.
As
with many of the tactics described here, the cumulative effects are
difficult to fully appreciate if you haven’t personally been on the
sharp end of them. Among other things, the tactic can be used to cause
sleep deprivation, which in turn can create additional problems, both
physical and psychological.
If
gang stalkers have access to a residence adjacent to that of the victim
(especially, for example, in an apartment building or condominium
complex), they can easily generate noises that will be heard only by the
target.
As
is typical of psychological operations tactics used by FBI minions,
harassment by noise is virtually impossible to prove. You could record
the noise, but you could not prove where and when you made the recording
– let alone where the sound came from or who was generating it.
Moreover, even if you could prove all of that, it would be difficult or
impossible to legally establish that the perpetrator was conspiring with
anyone else to deliberately harass you.
High-Technology Noise Harassment: Hypersonic Sound
In
an organized stalking operation, harassment by noise can be much more
sophisticated than simply banging on the wall or playing loud music.
Sound projection technology developed in 1990s can generate noise which can only be heard by the person being targeted.
This technology – called “hypersonic sound” –
involves using a processor to convert a sound into a complex ultrasonic
signal (that is, beyond the range of human hearing). Unlike sound from a
conventional audio speaker, the sound travels in a column rather than
spreading out, so its direction can be precisely controlled. You will
only hear it if your ears are inline with the sound column – or if the
signals is bounced off a hard surface.
If
a victim of organized stalking tells others about sounds that he or she
hears – but which no one else hears – it is a safe bet that the
individual will be viewed as crazy. That makes this a perfect weapon for torturing someone psychologically because it can destroy the victim’s credibility along with his or her sanity.
In
addition, the skeptical responses to the victim’s attempts to describe
such harassment will almost certainly cause the victim to become
intensely angry – which will further errode the victim’s mental health.
If you are a victim of this type of harassment, you might want to direct your friends and relatives to these two sources:
This document from a corporation that markets the technology has a clear explanation of how it works:
Hypersonic Sound
This TV program features
an interview with an engineer describing and demonstrating how such
devices work. The relevant segment begins at minute 20.
As
explained in the “Tactics For Fighting Back” page of this website,
noise-reducing headphones can provide some relief from noise harassment;
however, the best response to such harassment (and to gang stalking
generally) is a low-tech offensive strategy: blanket your neighborhood
with flyers (either by mail or hand-delivery or both) and send emails to
all local officials, news outlets, churches, schools, Congress members,
etc. calling attention to this form of domestic terrorism (gang
stalking).
Other High-Tech Gadgetry: Invisibility (Seriously)
Other
exotic technologies are also used by the sociopaths in America’s rogue
alphabet agencies (and their parasitic intelligence-security contractor
firms). An interesting example was described in the well-researched
cover article by Robert Guffey about “state-sponsored gang stalking”
published in the October 2013 issue of Fortean Times.
In
1987 an American electronics engineer, Richard Schowengerdt, began
experimenting with “electro-optical-camouflage.” In 1994 he patented
this “cloaking” technology – also called “invisibility technology.”
The Fortean Times article describes
how that technology was apparently used in a gang stalking operation by
the U.S. government to psychologically torture a criminal suspect by
enabling stalkers to lurk in the victim’s residence unseen.
The
facts of that case suggest that the perpetrators were federal agents
testing the technology – and presumably indulging their sociopathic
tendencies.
Of
course, there is no reason to think that such technology is being
widely used. I include the information here mainly because (a) it was
apparently used in gang stalking by the U.S. government as documented in
a well-researched published article, and (b) it gives you an idea of
the level of technology available for surveillance and psychological
warfare in state-sponsored gang stalking.
For anyone specifically interested in invisibility technology,
here is another article – published in December 2013 – about a similar technology being developed in China.
Other High-Tech Gadgetry: Seeing Through Walls
Internal
documents from the Cointelpro era proved that the FBI secretly used
illegal “black bag jobs” (breaking into the residences of targeted
individuals) to perform surveillance and to perpetrate psychological
warfare – such as the tactic of “gas-lighting” described earlier.
Although
the tactic is just as illegal now as it was then (invasive spying
without a search warrant), it is apparently used routinely in gang
stalking, based on virtually all victim accounts.
Consequently,
it would be very easy to deploy miniature spy cameras (which are now
very advanced and small and inexpensive) in the victim’s residence. So
the use of technology which can see through walls is probably
unnecessary in most cases, but the technology does exist.
A June 2005 article in Popular Mechanics by
Frank Vizard stated that “through-the-wall” technology “has been
aggressively researched by military and university labs since the
mid-1990s.” The article is on page 30.
Click here to view a pdf file of the magazine:
This August 2012 article in Popular Science describes
a form of this technology which uses Wi-Fi radio signals – which are
now available in most U.S. homes. Reportedly, Wi-Fi radar can
“determine a person’s location, speed, and direction – even through a one-foot-thick brick wall.”
Such
technology could be perfect for gang stalking because, as the article
notes, the device cannot be detected, since it does not emit any radio
waves.
Other High-Tech Gadgetry: Directed-Energy Weapons (DEWs)
“For
years, the U.S. military has explored a new kind of firepower that is
instantaneous, precise and virtually inexhaustible: beams of
electromagnetic energy. “Directed-energy” pulses can be throttled up or
down depending on the situation, much like the phasers on “Star Trek”
could be set to kill or merely stun….
The
hallmark of all directed-energy weapons is that the target — whether a
human or a mechanical object — has no chance to avoid the shot because
it moves at the speed of light. At some frequencies, it can penetrate
walls.”
A
Directed-Energy Weapon (DEW) emits energy at a target without using a
projectile, and can produce a variety of lethal or non-lethal effects.
Such weapons have existed for decades, and are used by militaries and
law enforcement agencies around the world. DEWs use various forms of
energy, such as laser beams, electromagnetic radiation, and particle
beams, as well as sound.
Weapons
of this type are often referred to as “non-lethal weapons” to
distinguish them from weapons such as knives, batons, firearms,
artillery, and such; however, the intensity of some energy weapons can
produce lethal effects.
Naturally,
much of the information about these weapons is classified. One example
of the publicly-available documents on the subject is the
previously-mentioned declassified Pentagon report about electronic
weapons (dated 1998) called
“Bioeffects of Selected Non-Lethal Weapons” – which was obtained via a Freedom of Information Act request.
Occasional references to the subject do appear in the news. An example is
this May 17, 2013 article in the
Marine Corps Times about the Joint Non-Lethal Weapons Directorate at Quantico, Virginia. The article explains that the directorate performs
“research
into everything from electroshock weapons to the Active Denial System, a
directed energy weapon that causes painful sensations to targeted
individuals without burning the skin.”
This September 2012 article in
Business Insider –
“America’s Scariest Weapons” – gives an idea of some of the electronics weapons being developed by the U.S. government, such as a “heat ray.”
If
you are interested in an example of how someone could construct a
homemade short-range electromagnetic weapon (for research purposes or
for self-defense or whatever),
this might be a good place to start.
That
is some of the non-disputed information about DEWs. The role of such
weapons in U.S. domestic counterintelligence operations is in the realm
of speculation and anecdotal evidence.
Many
descriptions exist on the Internet which purport to be accounts by gang
stalking victims claiming to have been attacked with such weapons.
Accounts include descriptions of burning sensations, headaches, nausea,
sudden fatigue, a fluttering sensation in the chest, etc.
My observations about DEWs and organized stalking:
(1)
The extensive use of disinformation by gang stalkers raises problems
when assessing the plausibility of claims about the use of DEWs against
targeted individuals. To the extent that the use of DEWs is perceived by
non-victims of gang stalking as being implausible, discussion of their
use (whether accurate or not) could undermine efforts to expose gang
stalking generally. Secondly, even if DEWs are rarely used, it could
further the counterintelligence objectives to discuss them on the
Internet, if only to raise the anxiety of victims, who might begin
wondering whether their headaches, high-blood pressure, and other
problems are being induced by DEWs.
(2)
It is inherently difficult to distinguish between some of the effects
of DEWs and the effects of psychological harassment (“psyops”) tactics.
Stress induced by psychological torment can manifest in some of the same
ways – accelerated heart rates and headaches, for example.
However…
(3)
The use of DEWs against gang stalking victims is technologically
plausible. No one disputes the existence of such devices, and they’re
consistent with the tactics of gang stalking. For example, harassment by
noises generated from adjacent residences is a common gang stalking
tactic, so it isn’t much of a stretch to imagine the use of energy
weapons in the same situation, as the energy would easily pass through
most walls.
(4)
Such a tactic would be a logical choice for use in organized stalking,
since it would be difficult or impossible to prove that such attacks
were happening.
(5)
Reportedly, the intensity and lethality of such weapons varies greatly,
but even the most extreme applications would be consistent with the
malevolent campaigns against gang stalking victims. Anyone willing to
terrorize someone relentlessly with psychological torment – even knowing
that it could lead to suicide or heart attack (or lethal violence by
the victim against others in response), would presumably not have moral
reservations about using DEWs.
(6)
My own personal contacts with self-proclaimed targeted individuals
include three cases in which persons whom I believe (for multiple
reasons) to be highly credible reported having apparently been attacked
by some form of non-lethal weapons.
Counter-measures
Since
the role of DEWs in organized stalking is surrounded by at least as
much disinformation as any other area of the subject, it is difficult to
know how widespread the use of such weapons could be – let alone how to
defend against them. The technical issues involved in possible
counter-measures are beyond my ken, but for what it is worth, a credible
source –
Wired – states
in this May 2012 article that a Faraday cage blocks all electromagnetic radiation.
A final note on the efficacy of gang stalking tactics
At the end of his aforementioned book Stopping a Stalker, retired police captain Robert L. Snow describes the psychological aftermath
of stalking.
Keep
in mind: Snow is describing the impact of being stalked by a single
individual with limited resources – not the long-term effects of being
stalked by numerous perpetrators with seemingly unlimited resources,
conspiring with each other across a criminal network which has the
support of the government and uses refined psychological operations
(“psyops”) tactics combined with high-tech surveillance.
“During
my 30 years as a police officer I have dealt with thousands of crime
victims, and have felt a deep compassion for the majority of these
people, who have been robbed, raped, shot, swindled, beaten, and
burglarized. Yet, by the time I saw these victims, the crime was over
and the healing process had already begun.
With
stalking victims, however, the crime wasn’t over with, but continued on
and on. Victims of stalking say the experience is like a prolonged
rape, a never-ending and terrifying loss of control over one’s life.
Stalking is one of the most psychologically crippling things that can
happen to a person. Being stalked takes away a person’s freedom, a
person’s security, and often a person’s will to live.”
__________________________________________________________
9. Mobbing and Workplace Violence
Mobbing is
the workplace harassment component of gang stalking. It is nothing like
the activity people commonly associate with terms like “workplace
harassment.” Common examples of harassment by employers include things
like sexual harassment or verbal abuse by a manager. Mobbing is a
systematic campaign of intense harassment by multiple co-workers and
managers, often (or perhaps always) done as part of the overall
surveillance and harassment process known as gang stalking.
The
objective of mobbing is to emotionally torture a targeted employee.
It’s done either to force him or her to quit or to keep the person
silent (in the case of potential whistle-blowers) or for vengeance when
the victim has enraged someone in the organization’s management
structure who has the necessary assets and connections to arrange for
the stalking (as in my own case).
The Connection between Mobbing and Workplace Violence
Honest
law enforcement personnel – as well as criminologists and groups such
as the ACLU – should be interested in the apparent connection between
mobbing and workplace violence.
Mass
shootings at places of employment and schools are sometimes referred to
as incidents of employees “going postal” – a reference to the fact that
a number of such reported cases involved U.S. Post Office employees.
Peer-reviewed
studies by Dr. Kenneth Westhues, Professor Emeritus of Sociology,
University of Waterloo, Canada, have found a link between mobbing (group
bullying) and mass shootings in recent years in North America in
workplaces and educational institutions.
As
noted in an article on NowPublic.com, the link between mobbing and
workplace violence “eluded authorities, university officials, and,
obviously, the mainstream media.”
“In
nearly every mass shooting, Westhues found that a programmatic system
of workplace or academic bullying had systematically isolated,
scapegoated and humiliated the victim and virtually groomed the shooter
for the role of monster. The role of psychiatry, police, and
administrative bureaucracy as “threat assessment teams” and “safety
prevention” was not only an utter failure, but, moreover, prompted the
very acts of mass violence they sought to prevent.”
This is a link to the NowPublic.com posting:
Below is a link to Professor Westhues’s report Mobbing and the Virginia Tech Massacre (November 2007)
“On
April 16, 2007, Seung-Hui Cho, a fourth-year student in the English
Department at Virginia Polytechnic Institute and State University,
murdered 32 professors and students and injured a further 25, then took
his own life….
Cho
appears to have been the target of an uncommon but distinct and
devastating social process called workplace mobbing. It is the
impassioned ganging up of managers and/or peers against a targeted
worker, the object being the target’s absolute humiliation and
elimination from respectable company.”
This
next link is to a website featuring correspondence between Professor
Westhues and attorney Keith Labella, discussing the apparent causal
relationship between mobbing and workplace violence “rampage killings.”
Westhues estimates that at least a third of all such incidents can be attributed to mobbing (systematic harassment).
Media Narratives about Workplace Violence and Mass Shootings
Reporting
and commentary on workplace violence incidents and mass shootings tends
to assume that these incidents are either unique unrelated events, or
that they are attributable to either the violence in our culture, such
as movies and video games, or the prevalence of firearms, or a general
moral decline in society, or a combination of these things.
The
more you learn about gang stalking and mobbing (especially if you have
experienced it first-hand), the more you start to wonder about the
extent to which it accounts for the workplace shootings reported in the
media.
As
with gang stalking generally, articles occasionally appear in the
mainstream press about the workplace harassment component of gang
stalking (mobbing).
This article from Newsweek/Daily Beast is a good example.
____________________________
An example of a case which deserves a closer look
To
cite one example (of many), a shooting in Long Beach, California
invites suspicion about the possible involvement of mobbing. Even if
there are other explanations, this particular case is interesting for
several reasons. Incidentally, at the time of this shooting, I lived
close to downtown Long Beach, and I witnessed some of the police and
ambulance activity associated with the event, and the (minimal) local
news coverage. Since I was aware of the incident, I became curious about
the relative silence about it in the media.
On
February 16, 2012, on the seventh floor of the Glenn M. Anderson
Federal Building in downtown Long Beach, Ezequiel Garcia, an agent of
Immigration and Customs Enforcement (ICE), shot his boss, Kevin Kozak,
six times. Reportedly (see the article linked below for details), Mr.
Garcia’s attack on his boss was in response to the fact that Mr. Kozak
(who was the second-in-command of ICE’s Los Angeles region) had
turned-down Garcia’s request for a transfer within the department.
Apparently,
Garcia shot Kozak “following a discussion about Garcia’s job
performance.” Another agent, Perry Woo, then rushed into the room and
fatally shot Garcia. Kozak survived.
Even
if this was not a case of mobbing, it is a workplace violence incident
which – despite involving two government officers being shot (one
fatally) in a federal building in the downtown area of a major city –
barely registered as a blip on the media’s radar. Furthermore, both ICE
and the FBI – which investigated the case – declined to provide any of
the details about what happened.
After
spending a year investigating the incident, the FBI determined that the
fatal shooting of Garcia was justified. As the CBS article below notes,
The FBI’s spokeswoman, Laura Eimiller, would only say that the details
about what led to the incident “would be kept confidential because no
criminal charges are planned.”
Apart
from several paragraphs in the middle of the article linked below, most
of the media did not seem to be curious about the incident – or about
the silence of the government agencies involved. Apparently the matter
did pique the interest of a few people other than myself though; the
article cites concerns about the secrecy surrounding the event expressed
by representatives of the Citizens for Responsibility and Ethics in
Washington (CREW) and the Open Government Project at the Electronic
Privacy Information Center (EPIC).
A
skeptic of gang stalking, applying Occam’s razor to the publicly known
facts of this incident could understandably conclude that it was simply a
case of work-related stress that erupted in violence – perhaps because
the persons involved were carrying firearms. However, if you accept the
theory – supported by all the information presented elsewhere in this
website – that America currently has a modern version of Cointelpro
(“gang stalking”) which involves mobbing, and which operates with the
acquiescence of law enforcement agencies (such as the FBI, ICE, etc.),
that at least raises the question of whether this was a case of mobbing.
Maybe
the ICE agent, Mr. Garcia, was just having a bad day. Perhaps someone
cut him off in traffic on his way to work that morning and he was a bit
wound-up about it, so he shot his boss six times during his job
performance review.
On
the other hand, maybe he snapped after a period of systematic
harassment, and the fed’s did not want that made public. At a minimum,
the case illustrates the secrecy which often surrounds the activities of
America’s law enforcement agencies.
____________________________
The mass shooting at the Washington Navy Yard in September 2013
A
website about gang stalking would not be complete without mentioning
this incident. News coverage of the shooting – and the public commentary
about it – included many references to speculation about the
possibility that the shooter had been the target of a gang stalking / MK
Ultra-type operation.
Here is what has been reported:
A
shooting rampage at the Washington D.C. Navy Yard on September 16, 2013
left a dozen people killed (13 including the shooter), and 8 others
wounded. Naturally, the shooting received extensive national news
coverage.
The
shooter, Aaron Alexis, had claimed to have been stalked by multiple
perpetrators and had reported that he was the victim of electronic
harassment and noise harassment tactics of the sort commonly described
by other self-proclaimed targeted individuals.
Alexis
even carved “My ELF Weapon” into the receiver of his shotgun, as seen
in this photo. ELF is a common abbreviation for “extremely low
frequency.”
The
incident involved other red flags for many observers. For example,
while some people suggested the voices Alexis reported hearing were
symptomatic of schizophrenia, others noted that schizophrenia typically
begins in early adulthood, roughly between the ages of 15 and 25.
Alexis, who was an information technology employee with a security
clearance at a defense-related computer company, was 34 years old. Also,
persons afflicted with schizophrenia are not typically violent; if
anything, they are more likely to be a danger to themselves.
It
should also be noted that Alexis never reported that he believed that
the voices he heard were coming from some supernatural source – which
would have been more suggestive of mental illness. His accounts were
much more consistent with the kind of sonic projection device
demonstrated here by an engineer who designs them. See the section which
begins at 20:08
of this video.
No
manifesto was left by the shooter citing any political or religious
agenda that might have motivated him to shoot twenty people at his
workplace. His words and actions are more plausibly explained by his
claim that he was in fact being systematically harassed, and he
eventually snapped.
Other
facts about the incident also drew suspicion. For example, the FBI
bypassed the ATF (the Bureau of Alcohol, Tobacco, Firearms and
Explosives) and performed their own trace of the shotgun used – even
though the ATF is the federal agency in charge of tracing guns used in
crimes.
An Associated Press article included this quote:
“I
have never seen an instance where ATF had not been relied upon to trace
the gun,” said Mike Bouchard, a former ATF assistant director for field
operations. “I have never heard of a situation like that.”
Since
the investigation of the shooting is being handled by the FBI – which
is notoriously secretive and has a history of perpetrating organized
stalking crimes against Americans (Cointelpro) – it is difficult to
guess how much critical information about the case is being kept secret
from the public.
Multiple news sources –
such as the New York Times –
made note of the curious timeline of events surrounding the shooting.
The shooter’s employer and the Newport Rhode Island Police Department
and the navy were all aware that Alexis had reported being harassed by
“voices” and noises, yet no one suspended his security clearance or
otherwise intervened.
Similarly
– and this has never been explained as far as I know – a tactical
response team of the Capitol Police was reportedly in the area at the
time, but was ordered to stand down (not participate in the police
response).
Here are some excerpts from
a BBC News report on September 18 which described the non-response:
Multiple
sources in the Capitol Police department have told the BBC that its
highly trained and heavily armed four-man Containment and Emergency
Response Team (Cert) was near the Navy Yard when the initial report of
an active shooter came in about 8:20 local time.
According
to a Capitol Police source, an officer with the Metropolitan Police
Department (MPD), Washington DC’s main municipal force, told the Capitol
Cert officers they were the only police on the site equipped with long
guns and requested their help stopping the gunman.
When the Capitol Police team radioed their superiors, they were told by a watch commander to leave the scene, the BBC was told.
The gunman, Aaron Alexis, was reported killed after 9:00.
A few days later,
a Congressman confirmed that
the local SWAT unit had been inexplicably ordered not to respond. Rep.
Michael McCaul (R-Texas) told CNN’s Jake Tapper that he personally spoke
with a SWAT team member who confirmed that they were told to stand down
(not respond) to the mass shooting at the Washington Navy Yard.
A week after the shooting,
The Washington Times (in their
Communities section) published an article exploring the gang stalking (electronic harassment) speculation surrounding the shooting.
Some
conspiracists suggest that Alexis was a “targeted individual,” or “TI,”
the term-of-art used by anguished people who believe they’re being
“gang stalked” by shadowy enemies, often in the government. The elements
of Alexis’ police report — covert microwave weapons, conspiracies and
sleep disturbances — are common elements in gang stalking accounts. (Of
course, they’re also common elements in schizophrenia.)….
The
microwave weaponry theory would be just as absurd as some of the other
conspiracies if the Pentagon hadn’t been researching the possibility of
using similar voice-projection technology in the past as a nonlethal
weapon.
According
to one report on the project, such a weapon would create a condition
similar to schizophrenia. “Application of the microwave hearing
technology could facilitate a private message transmission. It may be
useful to provide a disruptive condition to a person not aware of the
technology. Not only might it be disruptive to the sense of hearing, it
could be psychologically devastating if one suddenly heard ‘voices
within one’s head.’”
Five
weeks after the mass shooting, news reports emerged that the shooter
had sent three emails to the group called Freedom From Covert Harassment
& Surveillance (FFCHS) – which is ostensibly a gang stalking
victims support group (although as explained in the web page about the
organization in this website, FFCHS is actually a disinformation front
group).
So
the fed’s – who apparently monitor everyone’s phone calls, emails, and
Internet activity – failed to intervene in any way despite the shooter’s
emails (and despite other obvious warning flags mentioned above) in a
case involving an employee with a security clearance who was working at
military facilities and reporting that he was being harassed and hearing
voices.
“[The
emails] also suggest that the bloody rampage was plotted as a revenge
attack against the US Navy — contrary to FBI statements that the former
sailor did not appear to have had a specific target.”
On November 20, 2013,
The Washington Times reported that
U.S. Rep. Darrell E. Issa (R-Calif.), chairman of the Oversight and
Government Reform Committee is seeking information from the Office of
Personnel Management (OPM) about the security clearance possessed by
Aaron Alexis:
“But Mr. Issa says OPM is refusing to turn over those documents and allowing them to be viewed only behind closed doors.”
In January 2014,
Politico reported that
a local NBC news journalist in Washington D.C., Scott MacFarlane,
received an email which the U.S. Navy sent to him by accident.
The
internal email – from the Navy’s FOIA (Freedom of Information Act)
office – outlined the strategy which they planned to use to limit the
amount of information released to MacFarlane, who had filed a FOIA
request for internal Navy memos sent on the day of the shooting.
MacFarlane tweeted about the incident with this message:
“EPIC FAILURE- U.S. Navy accidentally sends reporter its strategy memo for dodging his FOIA request”
He included this screenshot of the email.
Click on image to enlarge
The
most charitable analysis would be that this was simply routine “cover
your ass” protocol for a government entity seeking to avoid embarrassing
revelations about its incompetent management of security at a naval
facility.
At least one thing seems clear: some reporters in the mainstream news media are still curious about the shooting.
____________________________
Theodore Kaczynski (“The Unabomber”)
A
series of bombings was perpetrated from 1978 to 1995 which killed three
people and injured 23 others. The bomber, a mathematician named
Theodore Kaczynski, was referred to as “the Unabomber” by the FBI before
they discovered his identity.
Kaczynski
wrote a manifesto which explained that his motive for the bombings was
to expose the threat to freedom posed by modern technology.
The
court rejected Kaczynski’s request to represent himself at his trial,
and made a plea agreement to avoid having Kaczynski possibly use his
trial as a public platform to express his views. In return for a promise
to not seek the death penalty, Kaczynski pleaded guilty, and was
sentenced to life in prison.
Those
facts are commonly known; what is less widely-known is that Kaczynski
was one of the subjects of the CIA’s secret mind-control experiments
program called MK Ultra while he was a student at Harvard University.
An article by Alston Chase
in the June 2000 issue of the Atlanticexplored
the question of whether Kaczynski’s violence was the result of his
psychological torture. Kacyzinski was recruited to participate in a
series of psychology experiments, and he was deceived about their true
nature, which was to examine the effects of extreme emotional stress –
possibly to help the CIA develop interrogation techniques.
The
article implies that the experiment could possibly have been a factor
in Kaczynski’s later acts of violence. Some excerpts from the article:
“There
is no evidence of immediate mental degradation in the project’s
aftermath. Emotional turmoil is another matter. As Sally Johnson, the
forensic psychiatrist, reported, Kaczynski clearly began to experience
emotional distress then, and began to develop his anti-technology
views.”
“It
is clear, also, that Murray’s experiment deeply affected at least some
of its subjects. From interviews conducted after the project ended, it
is apparent that certain students had found the experience searing.”
“When,
soon after, Kaczynski began to worry about the possibility of mind
control, he was not giving vent to paranoid delusions. In view of
Murray’s experiment, he was not only rational but right. The university
and the psychiatric establishment had been willing accomplices in an
experiment that had treated human beings as unwitting guinea pigs, and
had treated them brutally.”
“Kaczynski felt that justice demanded that he take revenge on society.”
The injuries and deaths of the 26 victims of Kaczynski’s bombs were quite possibly “collateral damage” from a secret and unethical U.S. government program.
_________________________________________________________
10. Selection of Targeted Individuals
“To
a hammer everything looks like a nail. To an intelligence agent,
informant, or law enforcement officer, everything unconventional or
unorthodox looks like at least a pre-embryonic terrorist danger.”
– Bruce Fein, U.S. Deputy Attorney General in the Reagan administration
In 2009 Bruce Fein advised Congress that
the national intelligence-gathering system of regional data fusion
centers should be abandoned. He compared the system to those operated by
the Soviet Union’s KGB and East Germany’s Stasi.
U.S. government’s terrorist watch list
The U.S. government’s Terrorist Screening Database is shrouded in secrecy.
A New York Times article in December 2013 reported that
at least 700,000 people were
on the federal government’s terrorist watch list, and that little is
publicly known about how the list is managed. Some excerpts from the
article:
“…the
government refuses to confirm or deny whether someone is on the list,
officially called the Terrorist Screening Database, or divulge the
criteria used to make the decisions…”
“The
Terrorist Screening Center, which administers the main terrorist watch
list, declined to discuss its procedures, or to release current data
about the number of people on various watch lists, and how many of them
are American citizens.”
Quotas for reporting suspicious persons
A piece at the gang stalking website
HomelandStalk.com called attention to
a report by an ABC local news affiliate in Denver in
July 2006 which revealed that some federal air marshals said they have
quotas for identifying a certain number of passengers as suspicious.
Air
marshals interviewed for the article said that if they wish to receive
positive performance evaluations, raises, bonuses, and special
assignments, they must regularly file Surveillance Detection Reports
(SDRs) – at least one per month according to some sources – about
passengers who supposedly behaved in a suspicious manner. Individuals
identified in such reports can end up in an international database watch
list.
While
it is unlikely that officials in charge of various homeland security
programs would publicly acknowledge the pressure on employees to name
persons as being suspicious, it is easy to imagine how that same
phenomenon could be manifested in various agencies, resulting in a sort
of “witch hunt” to rationalize the budgets and powers of the homeland
security bureaucracy.
Black-listing by brown-nosers
In a September 2004 article in the Sociological Forum,
David Cunningham and Barb Browning at Brandeis University analyzed the
selection of individuals targeted by the FBI’s original Cointelpro
operations. The article begins with this quote from Frank Donner’s The Age of Surveillance:
“The selection of a target embodies a judgment of deviance from the dominant political culture.”
In
essence, the authors found that FBI agents responded to organizational
pressure from the upper echelon of the FBI by rationalizing the
targeting of individuals for surveillance and subversion – even when those individuals were not engaged in subversive political activities.
They did so by pointing to characteristics of the targets which the
agents knew their senior officials regarded as culturally objectionable:
“…field
agents drew upon particular culturally resonant signals of deviance to
demonize and subsequently act against SDS members even in the absence of
threatening political activity.”
Agents
were trying to curry favor with a small group at the top of the agency –
the directorate – who “made the final decisions about all
counterintelligence actions.”
Targeting terrorist suspects and government whistle-blowers
According
to some published mainstream news reports, individuals are sometimes
targeted for gang stalking because they are suspected of involvement –
or potential future involvement – in terrorism or crime, but are not
implicated by any legal evidence. For example, see
the May 31, 2006 article in the Canadian national newspaper,
The Globe and Mail, regarding such tactics being illegally used in Canada.
Other
mainstream news reports indicate that gang stalking is also used by
intelligence agencies to punish or intimidate whistle-blowers – for
example, as reported in
the October 10, 2004 article in
the Sunday Times, a major newspaper in the U.K., about the use of gang stalking by the intelligence agency MI5.
Targeting individuals for experimental or training purposes
Some
unlucky individuals might be targeted essentially for
counterintelligence psyops research or training purposes (even if they
are ostensibly chosen for some more “legitimate” security reasons).
If
you doubt that is plausible, read about the CIA’s MK Ultra experiments,
in which many American (and Canadian) citizens were used as human
guinea pigs.
Targeting individuals for extra-judicial punishment & experimentation
A well-researched article in the
October 2013 issue of Fortean Timesdocumented
a case of state-sponsored gang stalking – described as such – in which a
former U.S. military member was apparently targeted both for the
purposes of extra-judicial punishment and to test psychological
operations technology.
Exploiting watch lists for personal vendettas and corporate agendas
In recent years, there have been media reports of something called
“swatting” –
in which an anonymous person – either for revenge or for amusement –
calls 911 and makes a false report of an emergency happening at the
address of a neighbor or enemy (or in some cases a celebrity) so police
will respond to the residence.
It
is not difficult to imagine how a more sophisticated and sinister
version of that tactic could be used by someone with connections to
America’s now-massive and secretive homeland security infrastructure, by
reporting someone as “suspicious.”
As
it is now structured, the U.S. law enforcement and intelligence
industry provides a perfect environment for abuse of power. The claim
that America faces a constant indefinite threat of terrorism has created
political cover for seemingly unlimited money and secrecy and power for
the agencies and private firms involved.
Increasingly sophisticated surveillance and “non-lethal” weapons technology makes the potential for abuse even greater still.
In
theory, organized stalking (counterintelligence subversion) could be
used against someone by an individual or a corporation in one of several
ways.
One
possibility is that a person who has either a personal or professional
connection to the law enforcement or intelligence industry could have
someone named as a “suspicious person” – for example, by submitting his
or her name to a Terrorism Liaison Officer (TLO). This might be easily
done by a member of InfraGard (the corporate-FBI alliance) or someone
with a friend or relative in an agency such as the FBI.
As
explained elsewhere in this website, we know from hacked emails of
intelligence-security firms and other sources that corporations hire
current and former spooks and law enforcement agents to do their
bidding, and that such work includes counterintelligence operations
(disinformation, infiltration, etc.). It is certainly possible that such
work also includes subversion (gang stalking).
Why would the feds allow non-governmental counterintelligence subversion?
Belgian
criminologist Nicolas Desurmont has published several academic articles
on state-sanctioned gang stalking (links are in the “Published
Articles” section of this overview).
In his 2006 article, Vers une problématique du harcèlement criminel en réseau,
Desurmont suggests that in at least some cases, gang stalking is a dual
system involving law enforcement agencies and criminal perpetrators,
which serves the interests of both groups.
For
most people, the notion that law enforcement and intelligence agencies
would be working with criminals – rather than pursuing them – seems
deeply counter-intuitive. Remember though, U.S. intelligence agencies
such as the CIA, routinely engage in criminal activity
according to the government itself – as explained in an earlier section of this overview (“Crimes by U.S. Law Enforcement & Intelligence Agencies”). Also,
law enforcement and intelligence agencies such as the FBI often authorize crimes by criminal informants. Moreover,
the Senate Church Committee found that during the original Cointelpro
operations, the FBI delegated acts of violence to organized crime
groups.
Desurmont
makes specific reference to the fact that the gang stalking acquiesced
in by the Belgian police includes acts of extra-judicial retribution.
Why would governments knowingly permit – and even assist – such criminal
stalking, as Desurmont describes?
One
reason is that outsourcing can create plausible deniability. If a
government agency contracts with a private firm – and then that firm
employs criminal informants to perform some of the dirty work – the
actual crimes can be several steps removed from officials.
Another reason would be to exploit a counterintelligence concept called
“a wilderness of mirrors.” The description – attributed to James J. Angleton,
the CIA’s Chief of the Counterintelligence from 1954 until 1974 – comes
from T.S. Eliot’s poem “Gerontion.” In essence, the idea is that
counterintelligence involves creating an environment in which it is
difficult to distinguish reality from illusion.
Having
a complex and opaque system of counterintelligence (CI) operations
serves the interests of the perpetrators – as does further obfuscating
the nature of the system by spreading disinformation.
Some
CI operations are handled directly by the FBI and other intelligence
agencies. Other CI activities are performed for the government by
private intelligence-security firms under government contract.
CI work is also done by such firms on behalf of large corporations. In
some cases – for example, the infiltration and subversion of the Occupy
Wall Street Movement – CI activities were performed by the FBI and by
private firms.
Using
criminal “informants” and civilian Stasi volunteers to perpetrate gang
stalking acts makes the whole process even more difficult to assess from
the perspective of victims and potential witnesses. Widespread use of
disinformation (discussed in detail in its own section of this overview
below) seeks to muddy the waters further with references to possible
involvement of mysterious cults and such.
One
advantage of having a variety of criminals involved (criminal
informants, sleazy private investigators, greedy unregulated
intelligence-security contractors, rogue intelligence agencies, useful
idiot vigilantes, cops who look the other way, etc.) is that it
presumably makes it easier for persons connected to the agencies and
corporations involved to use CI subversion as a personal weapon by
someone connected with one of those groups.
Official rationale for counterintelligence subversion
Merely
invoking the magic phrase “national security” seems to provide
sufficient legal and political justification these days for almost any
secret policy of the intelligence community. Even in
the rare caseswhen
the U.S. government’s “Star Chamber” – the secret FISA Court – rules
that a policy is out of bounds, Americans are not permitted to know what
the feds were trying to get away with.
As
practiced, organized stalking is essentially an extra-judicial
punishment, and it grossly violates multiple state and federal laws.
However, the policy is presumably justified – at least unofficially –
within the FBI and DOJ as being a legitimate counterintelligence policy
needed to subvert individuals who would otherwise pose a threat.
As
explained later in this overview (in the section on the U.S. Department
of Justice), probably the closest thing to an official public statement
of the philosophy behind targeting certain individuals was expressed in
the policy statement of the now-defunct “Weed and Seed” program. That
program’s description suggested a law enforcement strategy of
identifying and removing undesirable citizens from neighborhoods through
a “community-based” law enforcement approach.
Who gets to declare someone a suspicious person?
Consider just one part of the massive “homeland security” infrastructure – electronic surveillance by the NSA.
In September 2013it
emerged that at least a dozen NSA employees had been illegally spying
on their spouses and partners. This was a small glimpse of the potential
abuses of power in the modern U.S. spy industry.
NSA whistle-blower
Edward Snowden explained that access to the U.S. police state’s weapons is not limited to high-level officials:
“Any
analyst at any time can target anyone. Any selector, anywhere… I,
sitting at my desk, certainly had the authorities to wiretap anyone,
from you or your accountant, to a federal judge, to even the President…”
Additional thoughts on how individuals are targeted
For more of my analysis of how individuals are chosen as targets for gang stalking, see my
May 28, 2013 entry in
the “Gang Stalking News” section of this website, in which I explain my
inferences from the fact that certain types of people are not chosen as
gang stalking targets.
__________________________________________________________
11. The Organizational Structure of Gang Stalking
“The
system of espionage thus established, the country will swarm with
informers, spies, delators [accusers], and all that odious reptiles
tribe that bred in the sunshine of despotic power; that suck the blood
of the unfortunate and creep into the bosom of sleeping innocence.”
– Congressman John Allen, during the debates
about the Alien and Sedition Acts of 1798.
_________________________
In
the shadowy world of gang stalking, it is difficult for the targeted
individual to know the exact nature of the organizational structure of
his or her enemies. From the victim’s perspective – especially when the
person first realizes that he or she is being systematically harassed,
it is virtually impossible to know exactly who the enemies are and how
they are conspiring with each other.
For
many victims, their situation remains opaque because of the vast
disinformation campaign they encounter when they attempt to ascertain
what is happening via Internet research.
As
I described in the introduction to this overview however, the basic
nature of the crime – namely, that it is a government
counter-intelligence program – is an unavoidable conclusion since the
apparent scope of the activity would make it impossible for it to be
undetected by America’s now-massive homeland security surveillance and
information-sharing infrastructure.
Gang
stalking’s organizational structure apparently involves a mixture of
personnel. At the top are government officials and agents in federal law
enforcement and intelligence agencies, who would need to at least
passively acquiesce in the program, if not orchestrate it. Several
levels of delegates below them would be needed to manage and perform
various operations.
The FBI’s original version of Cointelpro also made use of local government and civilian minions.
A Los Angeles Times account of one of the Cointelpro operations explained that
“the
bureau had enlisted a local police chief, letter carriers and a
switchboard operator at Swathmore College to spy on campus and black
activist groups in the Philidelphia area.”
Presumably,
one major difference between the structure of the original Cointelpro
operations and modern gang stalking is the huge number of private
intelligence/security firm contractors with secret clearances now
employed by “homeland security” programs and corporations.
Intelligence/Security Contractors (“Surveillance Role Players”)
Among
the explicit goals of post-9/11 national security reforms was to
establish better cooperation between different government agencies, as
well as between federal and local jurisdictions. This was done partly to
reduce the problem of hoarding (“stove-piping”) information within
different agencies.
To
enable the sharing of information – for example by a national network
of “data fusion centers” – and to support a larger security
infrastructure generally – the role of security/intelligence/military
contractor firms was greatly expanded.
In
addition, law enforcement and intelligence agencies in the U.S. have
blurred the boundaries between public agencies and private contractors.
Not only do they work closely together, but there is also a lucrative
revolving-door career path for employees between the public and private
spheres.
Incidentally,
the collusion of corporations and federal agencies in the area of
domestic intelligence activities is not new. The U.S. government has
been colluding with big corporations to spy on Americans since the dawn
of the Cold War,
as this article in Wired notes, although the practice has greatly expanded.
“The
government is increasingly using corporations to do its surveillance
work, allowing it to get around restrictions that protect the privacy
and civil liberties of Americans, according to a report released….by the
American Civil Liberties Union…”
Cointelpro
Version 2.0 (gang stalking) apparently makes use of the large supply of
Americans who possess security clearances – currently nearly 4.9
million people
– almost a quarter of whom work for private firms.
A June 2013 article in USA Today noted that about 1.4 million Americans have security clearances of the top-secret class.
As
with other intelligence functions these days, one would expect that
there might be a large role for private contractors with security
clearances in managing organized stalking operations, and that does seem
to be the case.
Here is an example of intelligence contractors employed as domestic spies.
Numerous online job listings for “surveillance role players” seek
applicants with active security clearances and training in
counterintelligence. Some of these ads advise applicants that they will
“coordinate with local law enforcement.”
These
appear to be evidence that federal law enforcement agencies have
largely outsourced these operations. I am unaware of any other plausible
explanation for such job ads. Nor am I aware of any plausible
alternative explanations of who would have the tactical skills,
technological assets, funding, law enforcement connections, and secrecy
incentives needed to perpetrate nationwide stalking operations involving
counterintelligence methods.
If
any readers of this website have any insights about the nature of these
jobs (which seem never to be discussed in the mainstream news media), I
welcome them. Obviously, it’s pure speculation from my perspective that
they are possibly connected with organized stalking, but such a
connection would neatly answer these three questions:
“What do surveillance role players do?”
“Who perpetrates organized stalking?”
“How do the stalkers maintain the secrecy of their operations?”
Gang
stalking crosses multiple boundaries: geographical, jurisdictional,
legal, and moral. My guess is that the participants are primarily
motivated by the financial benefits, but also by the notion that they
are part of a secret group which is essentially above the law, and which
imposes what they see as a moral punishment on dissidents. They are
America’s more cowardly and more secretive version of the Taliban.
Criminal “Informants”
U.S.
law enforcement and intelligence agencies make extensive use of
criminal informants – who are never in short supply in a nation with one
of the highest per capita incarceration rates in the world. For the
purposes of counterintelligence stalking, “criminal informants” are
ex-convicts whose “informant” duties are spying on and harassing
targeted individuals.
Based
on my own observations and accounts of other targeted individuals, most
street-level perpetrators are rotated by the persons coordinating the
harassment, so the victim is not confronting the same individuals
repeatedly. Even though a victim might be harassed daily, most of the
stalkers only have a single instance of direct contact with the victim.
Some
websites about gang stalking contain speculation (and deliberate
disinformation) that suggests organized stalking is perpetrated by
criminal syndicates or secret fraternal orders. Supporting evidence for
this sometimes includes anonymous “confessions” by people who claimed to
have participated in such organizations.
It
is true that the U.S. Senate’s Church Committee found that the original
FBI Cointelpro operation sometimes employed members of the Mafia to
commit certain crimes, but it does not seem plausible that a large-scale
contemporary counterintelligence program could be controlled and kept
off the public radar if it were not being tightly managed by government
personnel with security clearances.
Terrorism Liaison Officers (TLOs)
Mainstream news reports show that since 2008, America’s “national security” personnel include
“Terrorism Liasion Officers.” TLOs
are firefighters, police officers, paramedics, and utility workers
trained to hunt for “suspicious activity” and report it to a secret
national government database.
As this
Denver Post article noted,
the “suspicious activity” could be simply taking photos or expressing
“extremist beliefs.” One of the concerns about this policy was expressed
by the director of the Electronic Privacy Information Center, John
Verdi:
”The
problem is, you’re drafting individuals whose job isn’t law enforcement
to spy on ordinary Americans and report their activities to the
government.”
If
you have a traditional (non-police state) view of America, you might
have difficulty wrapping your mind around the notion that firefighters,
paramedics, and utility workers are – or should be – gathering
information on their fellow Americans. For an example of the thinking
behind the concept – and an overview of the main elements of the
national intelligence-gathering infrastructure – you can read the
following document.
This
is a Naval Postgraduate School master’s thesis written in 2012 by
Joshua M. Dennis, a Chicago Fire Department chief. In his thesis, Mr.
Dennis seeks to clarify the role of the U.S. Fire Service in the
domestic intelligence community.
Apparently,
a pilot program for gathering and sharing information by firefighters
was launched by the U.S. Department of Homeland Security (DHS) in 2006,
but the national framework for spying (“suspicious activity reporting”)
by first-responders has not been fully worked out.
Hat-tip to the blog Cryptoscatology for posting the link.
InfraGard & DSAC Members (the corporate equivalent of TLOs)
As mentioned in the introduction of this overview, two corporate associations – InfraGard and DSAC –
have partnerships with the FBI and Homeland Security to share
intelligence. Apparently, certain trusted individuals in the
participating corporations are granted special membership status by the
FBI – complete with ID cards – and have privileged access to information
and direct communication with the FBI.
As
a practical matter, this very likely means that if one of these elite
members of the business community decides to have someone targeted for
an “investigation” they could simply tell the FBI that they have
concerns that the individual represents what counterintelligence agents
call “an insider threat” – meaning that an employee is suspected of
being likely to steal proprietary information or that he or she is a
“disgruntled employee” or has “extremist beliefs” and poses a safety or
national security risk.
For a detailed explanation of this unholy alliance, I recommend reading
this May 2013 report from
the Center for Media and Democracy (which reported that certain
corporations were/are exploiting this arrangement to use the FBI as a
weapon against their political adversary, the Occupy Wall Street
Movement.
I also strongly recommend watching
this episode of
a TV series by Jesse Ventura, in which he confronts a member of
InfraGard regarding some of the obvious potential for abuse of power
inherent in this arrangement. The relevant section begins 25 minutes
into the video.
Citizen Spies
Clearly
the government also makes extensive use of citizen informants. An
obvious example of this was the Department of Homeland Security’s policy
introduced in 2010 encouraging citizens to report anything suspicious (
“If you see something, say something”).
State and local governments have followed the feds’ lead (and money)
and made efforts to encourage a “snitch culture” – such as
this
Florida program encouraging residents to spy on their neighbors.
Based
on my own observations and on speculation about what would be a logical
(and in some cases necessary) use of resources for a
counterintelligence operation, it seems that some of the people who
participate – at least in small ways – in the stalking are civilians who
are presumably told they are assisting in an investigation or a
“neighborhood watch” type program.
No
doubt such neighbors of the targeted individual would not think of
themselves as “vigilantes” even though they are in fact participating in
an illegal conspiracy designed to inflict severe emotional and
financial extra-judicial punishment.
As noted in
“The Hidden Evil” by Mark Rich and
other sources, the motivations of the stalkers who actually perform
acts of harassment can be completely unrelated to the reason the
targeted individual was blacklisted in the first place. While the victim
may have been targeted simply because he or she crossed someone with
connections and money, the perpetrators – including the victim’s
neighbors, associates, relatives, etc. – can simply be told various lies
about the victim. Those lies can be tailored to fit the particular
person or groups of persons being recruited to participate in the
harassment.
As
for involvement by local law enforcement officers (and I can personally
attest to this), it sometimes involves direct participation (such as
being closely followed by patrol cars), and other times it simply
involves police “looking the other way” as others do the stalking.
As
I note in the section of this website about tactics for fighting back,
victims can exploit the fact that police do not want to get (officially)
involved – for example, by saturating their neighborhood with flyers
about gang stalking. My own massive use of that tactic never led to
local police responding (at least not in any direct public way), no
matter how indiscrete I was about it.
Even
if such tactics do not completely stop the harassment, they could
diminish it as the perpetrators become aware that their efforts will
result in very public exposure. Also, such tactics will help expose the
larger conspiracy to the general public – which will eventually
undermine the whole Stasi operation.
So the list of participants in the overall process of which organized stalking is an element probably looks something like this:
1) Officials & agents of law enforcement & intelligence agencies (DOJ, FBI, DIA, etc.)
2) Intelligence contractors with security clearances (“surveillance role players”)
3) Members of InfraGard & DSAC
4) Private investigators – for example, PIs employed by InfraGard/DSAC members
5) Terrorism Liaison Officers (firefighters, police officers, paramedics, & utility workers)
6) Other local police officers
7)
Civilian volunteers – neighbors, landlords, merchants, and others whose
assistance is obtained by informing them they are participating in an
investigation or a neighborhood watch program. Probably many of these
people are essentially “useful idiots” who are unaware of the exact
nature of the operations they’re assisting.
8) Criminal “informants” who are coerced and/or paid to administer the street-level harassment
9) Others (?) – For example, persons informally recruited to assist – such as friends, relatives, and business associates of persons in one of the other categories
__________________________________________________________
12. Social Conformity and Obedience to Authority
Nazi soldiers invading Poland
People
like to believe that the evil and stupid obedience displayed by people
such as Hitler’s followers is far-removed from their own nature and
culture. History and science say otherwise.
Anyone
wishing to understand gang stalking – or even to assess the
plausibility of such a conspiracy – should briefly review the
interesting (but disturbing) historical and scientific evidence on
conformity and obedience.
History
is filled with shocking manifestations of group-think – such as the
Salem, Massachusetts witch trials. Examples of blind deference to
authority include attrocities such as the “Rape of Nanking” in the
1930s, in which Japanese soldiers, sanctioned by their leaders, raped,
tortured, and murdered thousand of Chinese civilians. Many infants were
killed in front of their mothers in that massacre; sometimes the
soldiers gouged-out the children’s eyes before killing them.
Literature
is similarly filled with helpful examples of the evil and idiocy
associated with group-think and obedience. William Golding’s Lord of the Flies is one iconic example.
Findings of psychology experiments
fully support the notion that it would not be difficult to recruit
people to participate in organized harassment of targeted individuals.
In
Asch’s experiments, students were asked to participate – along with
others – in what was ostensibly a “vision test.” Actually, the other
participants were accomplices of the experimenter, and the study sought
to find how the unsuspecting students would be influenced by the
behavior of the others.
When
asked to assess the relative lengths of lines displayed on cards,
unsuspecting students were frequently influenced by the responses of the
accomplices around them. In other words, people often changed their
beliefs about what they had seen when the group expressed an opinion at
variance with their own. In a control group, with no pressure to
conform, few of the subjects gave incorrect answers. A majority (75
percent) of the subjects gave an incorrect answer to at least one
question when surrounded by others expressing the wrong answer.
“The disappearance of a sense of responsibilityis the most far-reaching consequence of submissionto authority.” – Stanley Milgram
In
Milgram’s experiments, participants were led to believe that they were
administering small electrical shocks to a person being tested, and that
the voltage was being incrementally increased with each delivery of the
shock. The experiment (and other similar subsequent experiments by
others) found that most people (61 to 66 percent) will administer a fatal electrical shock to an innocent person purely out of deference to authority.
Anyone
skeptical – despite such findings – about how easy it is to manipulate
average citizens to do very bad things to people they don’t know should
watch the video clip of
an ABC TV program on
the subject, which I included in the “Gang Stalking Videos” section of
this website. That video features a private investigator-type person
(not unlike the people who manage gang stalking operations presumably)
portraying himself as a law enforcement officer, and easily persuading
people to participate in serious crimes against strangers.
Chris Hedges on the morons who infest the U.S. military-intelligence industrial complex
As
a former member of the U.S. armed forces, I can say with some authority
that many of the personnel in our nation’s military are good people who
have both integrity and intelligence.
Unfortunately,
a large portion of the personnel – and I’m sure this also applies to
our intelligence agencies such as the FBI and CIA – are exactly the type
of folks described by journalist Chris Hedges in the article linked
below.
Just
as importantly, persons of the type Hedges refers to are no doubt
well-represented among the civilians who are manipulated into
participating in gang stalking.
Both
the achitects of gang stalking and the minions who perpetrate the
street-level harassment are careerist robots and butt-kissers.
Hedges,
who spent a couple of decades as a war correspondent, explains the
mentality and character of America’s Stasi supporters perfectly:
“Most
institutions have a propensity to promote mediocrities, those whose
primary strengths are knowing where power lies, being subservient and
obsequious to the centers of power and never letting morality get in the
way of one’s career. The military is the worst in this respect. In the
military, whether at the Paris Island boot camp or West Point, you are
trained not to think but to obey. What amazes me about the military is
how stupid and bovine its senior officers are. Those with brains and the
willingness to use them seem to be pushed out long before they can rise
to the senior-officer ranks. The many Army generals I met over the
years not only lacked the most rudimentary creativity and independence
of thought but nearly always saw the press, as well as an informed
public, as impinging on their love of order, regimentation, unwavering
obedience to authority and single-minded use of force to solve complex problems.”
__________________________________________________________
13. The U.S. Department of Justice (DOJ) and Gang Stalking
The moral character of the DOJ
“A
fish rots from the head down” – whether it’s the Vatican covering up
decades of child sex abuse by priests or the current head of the DOJ (as
I update this in November 2013) – U.S. Attorney General Eric Holder –
apparently doing whatever pleases the President and the law enforcement
and intelligence communities.
The
DOJ oversees federal law enforcement agencies such as the FBI and the
DEA, and apparently acquiesces in a contemporary version of Cointelpro
(organized stalking) – just as they did in the original version of that
program.
Corruption
at the U.S. Department of Justice is a bipartisan phenomenon. In 1971,
when civilian activists leaked secret FBI documents to
the Washington Post which
revealed crimes committed against Americans by the FBI, U.S. Attorney
General John Mitchell (who later served prison time for his role in the
Watergate scandal)
asked the Post’s executive editor Ben Bradlee not to disclose the documents. To his credit, Bradlee chose patriotism and truth over the imperatives of the corrupt police state thugs.
U.S.
Attorney General Eric Holder is a good example of the kind of people
who often infest the highest echelons of societies’ power structures,
and whose participation in counterintelligence operations would not be
out of character.
When
Holder was President Clinton’s deputy attorney general he approved the
pardon of Marc Rich – a wealthy investor who was indicted on 63 counts
of tax evasion and other charges and fled to Switzerland to avoid
prosecution. By all serious accounts, the only reason Clinton granted
the pardon was that Rich’s wife was a big donor to the Democratic Party.
Even
the opinion writers for the Washington Post – which is typically
sympathetic to the Democrats – said the pardon should have precluded
Holder from becoming President Obama’s Attorney General.
Richard Cohen wrote of the pardon:
“It
suggests that Holder, whatever his other qualifications, could not say
no to power. The Rich pardon request had power written all over it — the
patronage of important Democratic fundraisers, for instance.”
More
recently, Holder’s morally-questionable actions have included
aggressive efforts to intimidate whistle-blowers and journalists trying
to expose government malfeasance.
James Goodale, a First Amendment lawyer who played a key role in the publication of the Pentagon Papers by the New York Times,
makes the case that Holder is essentially treating reporters as criminals.
Federal Judges Report Frequent Lying by DOJ Prosecutors
Most
Americans give little thought to their nation’s Department of Justice,
except perhaps for high-profile cases with partisan political
implications. Evidence of the DOJ’s lack of integrity does not usually
show up on the public’s radar.
Federal
judges however, often see examples of the moral rot at the DOJ, and
have warned for decades that frequent misconduct by prosecutors
undermines Constitutional protections of individuals’ rights.
A September 2010 article in USA Today reported
on the effectiveness of a law enacted by Congress in 1997 intended to
curb illegal conduct by prosecutors, such as lying and deliberately
concealing evidence:
“…USA
TODAY documented 201 criminal cases in the years that followed in which
judges determined that Justice Department prosecutors — the nation’s
most elite and powerful law enforcement officials — themselves violated
laws or ethics rules.
In
case after case during that time, judges blasted prosecutors for
“flagrant” or “outrageous” misconduct. They caught some prosecutors
hiding evidence, found others lying to judges and juries, and said
others had broken plea bargains.”
Why
would federal prosecutors engage in misconduct? Part of the explanation
is that when they get caught, they are unlikely to be fired – as noted
in
another article by USA Today, which also found that
“the Justice Department consistently conceals its own investigations of misconduct from the public.”
Lying by the FBI
Since
the DOJ oversees the FBI, it is not surprising that the latter also
takes a very elastic view of its obligation to abide by the U.S.
Constitution. One way they do this is to assert, when caught lying, that
the deception is being done in the name of “national security.”
When
various American Islamic organizations and individuals filed a FOIA
(Freedom of Information Act) request in 2006 to determine if the FBI had
engaged in illegal surveillance of them, the FBI concealed the
existence of much of the material requested. In a lawsuit which
followed, the 9
th Circuit Court of Appeals found that
the FBI lied to the plaintiffs and to the court about the existence of the documents sought.
When
confronted with their deception, the FBI argued, in effect, that the
agency should not be required to tell the truth in court if they feel
that doing so could compromise national security interests. The court
rejected that claim.
Anyone
wondering about the plausibility of claims that federal law enforcement
agencies acquiesce in gang stalking should consider the fact that such
agencies sometimes explicitly assert that they are above the law.
DOJ’s Complicity in Spying and Lying by Private Intelligence Firms
Members
of the Anonymous movement hacked into the emails of the cybersecurity
firm HB Gary Federal In February 2011 after an executive at that firm
boasted in the Financial Times that his company had infiltrated Anonymous and started to expose them.
One
of the reports contained in the emails was a plan for HB Gary to work
with several other security firms to destroy the whistle-blower
organization WikiLeaks. News reports had indicated that Wikileaks was
planning to publish documents showing possible corruption and fraud at
Bank of America, so
the bank funded a “counterespionage” campaignagainst
Wikileaks, which included hiring the large intelligence contractor firm
Booz Allen, whose staff includes many former top officials from the
intelligence community and the defense department.
One
of the proposals was to create and plant fake documents to discredit
Wikileaks. The plans also included hacking into Wikileaks’ computer
systems. Another proposal was to “attack” and “disrupt” the career of
journalist Glenn Greenwald to pressure him into abandoning his public
support of Wikileaks.
Bank
of America had hired the law firm Hunton & Williams – among the
most well-connected law firms in the nation’s capital – to coordinate
the bank’s war against Wikileaks
at the recommendation of the DOJ.
Glenn
Greenwald explained the serious implications of this network of
government and corporate players in the private espionage business in a
February 2011 article for Salon.com:
“What
is set forth in these proposals for Bank of America quite possibly
constitutes serious crimes. Manufacturing and submitting fake documents
with the intent they be published likely constitutes forgery and
fraud. Threatening the careers of journalists and activists in order to
force them to be silent is possibly extortion and, depending on the
specific means to be used, constitutes other crimes as well. Attacking
WikiLeaks’ computer infrastructure in an attempt to compromise their
sources undoubtedly violates numerous cyber laws.
Yet
these firms had no compunction about proposing such measures to Bank
of America and Hunton & Williams, and even writing them down. What
accounts for that brazen disregard of risk? In this world, law does
not exist as a constraint. It’s impossible to imagine the DOJ ever,
ever prosecuting a huge entity like Bank of America for doing something
like waging war against WikiLeaks and its supporters. These massive
corporations and the firms that serve them have no fear of law or
government because they control each.”
As
Greenwald notes, a clear example of the extent to which the DOJ serves
corporate interests rather than the interests of justice and the
American public is the department’s very different reactions to the
cyber attacks on corporations versus an attack on Wikileaks:
“After
Anonymous imposed some very minimal cyber disruptions on Paypal,
Master Card and Amazon, the DOJ flamboyantly vowed to arrest the
culprits, and several individuals were just arrested as part of those
attacks. But weeks earlier, a far more damaging and serious cyber-attack was launched
at WikiLeaks, knocking them offline. Those attacks were sophisticated
and dangerous. Whoever did that was quite likely part of either a
government agency or a large private entity acting at its behest. Yet
the DOJ has never announced any investigation into those attacks or
vowed to apprehend the culprits, and it’s impossible to imagine that
ever happening.
Why? Because
crimes carried out that serve the Government’s agenda and target its
opponents are permitted and even encouraged; cyber-attacks are “crimes”
only when undertaken by those whom the Government dislikes, but are
perfectly permissible when the Government itself or those with a
sympathetic agenda unleash them.”
The
report explains that major U.S. corporations are using spies to conduct
surveillance (sometimes illegally) of non-profit organizations engaged
in advocacy for causes such as anti-war policy, consumer rights,
environmentalism, animal rights, and arms control.
Corporations
engaging in this kind of espionage reportedly include Wal-Mart,
Monsanto, Bank of America, Dow Chemical, Kraft, Coca-Cola, Chevron,
Burger King, McDonald’s, Shell, BP, and others – as well as the U.S.
Chamber of Commerce.
“…these corporations employ former CIA, National Security Agency and FBI agents to engage in private surveillance work, which is often illegal in nature but rarely — if ever — prosecuted.”
America’s Post-Constitutional Law Enforcement Paradigm
A
confluence of developments over the past couple of decades has led to a
more militarized and secretive form of law enforcement in America. A
counterintelligence subversion strategy of organized stalking is among
the most extreme manifestations of the new paradigm.
The
government’s natural tendency to expand its size and power has been
accelerated by the politics, profits, and career opportunities
associated with the “War on Drugs” and the “War on Terrorism.” At the
same time, advances in technology have made possible highly invasive
surveillance tools which create a constant temptation for abuse by
people in the intelligence, law enforcement, and security industries.
Another
development has been an erosion of traditional jurisdictional
boundaries in law enforcement. By design, numerous federal and local law
enforcement and intelligence agencies now work more closely with each
other, and with the private contractors who provide much of the
infrastructure, such as defense industry firms and private security
firms.
U.S. law enforcement agencies rely heavily upon criminal informants – despite the obvious conflicts of interest that involves.
Budgets and audits cited in the New York Times for
example, showed that the FBI was using more than 15,000 secret
informants in 2008, and the DEA (Drug Enforcement Adminstration) had
about 4,000 criminal informants on its payroll in 2005.
By
my own observations, and by anecdotal reports of others, gang stalking
apparently makes extensive use of criminal informants. But those
snitches are not being used by the FBI just to spy and inform; they are
perpetrating acts of criminal harassment for the purposes of
counterintelligence subversion.
Rather
than working to ensure the protection of Americans’ rights in this new
Big Brother surveillance environment, the U.S. Department of Justice has
done everything possible to enable the executive branch to increase its
secrecy and power at the expense of Americans’ civil liberties.
A
variety of Orwellian legal weapons have emerged – always based on
claims of national security. “Suspicious Activity Reports” are now filed
by “Terrorism Liaison Officers” and sent to a network of regional “Data
Fusion Centers” and reviewed by agents at the “Homeland Security
Department.”
Old-fashioned
concepts in the Bill of Rights – like obtaining search warrants from
judges – have been tossed aside. Now the FBI can just issue a “National
Security Letter.” Instead of launching an investigation based on
probable cause, the FBI can now just target an individual for
surveillance and investigation by calling it an “assessment.”
Concerning
other elements of the now-massive U.S. spy network, the public can only
speculate. For example, no one has yet said publicly what is being done
by the numerous “surveillance role players” (discussed elsewhere in
this website) with secret clearances and counterintelligence training
who are employed by intelligence-security contractors.
If
anyone challenges the Constitutional legitimacy of any of these
suspicious policies (or if members of the government question other
secret policies whose existence is unknown to the public), the matter is
referred to the U.S. government’s “Star Chamber” – the secret FISA
Court,
which in nearly all cases simply rubber-stamps the policy to maintain the façade of legitimacy.
The DOJ’s Index of Crimes
As mentioned in the introduction to this overview, claims about the widespread existence of gang stalking are supported by the
DOJ’s own crime survey statistics (obtained
via a Freedom of Information Act request) which showed that in 2006
there were an estimated 446,790 stalking incidents involving three or
more perpetrators stalking a single individual.
Claims about gang stalking are also supported
by the fact that the National Center for Victims of Crime – which is funded by the DOJ – apparently receives “thousands of calls per month” about such crimes. Yet organized stalking is conspicuously absent from the DOJ’s Index of Crimes.
As previously mentioned, Robert L. Snow, a retired police captain from the Indianapolis P.D., wrote a book called Stopping a Stalker,
in which he devoted a chapter to the subject of organized stalking by
multiple perpetrators associated with causes (“cause stalking”) – such
as stalking by extreme anti-abortion activists.
However, the entire subject of organized stalking
(or “group stalking,” “vigilante stalking,” etc.) does not appear in the DOJ’s website – even though the site includes
a comprehensive index of types of crimes and legal issues, including some that are relatively obscure.
The DOJ’s “Weed and Seed” Program
The
most interesting section of the DOJ website’s crime index – in relation
to the government’s apparent acquiescence in gang stalking – is a
reference to a program called “Weed and Seed.” The program name was
still in the index the last time I checked, but the information for that
section – which was part of something called the “Community Capacity
Development Office” (CCDO) no longer existed. Elsewhere in the website
was a statement explaining that the CCDO was closed due to lack of
funding:
“As
of June 5, 2011, the Community Capacity Development Office (CCDO)
closed due to a lack of federal funding for the office. For Fiscal Year
2012 Weed and Seed grants, the Bureau of Justice Assistance will manage
these grants until the end of the grant award period.”
I
copied the Weed and Seed program’s description while it was still on
the website (in February 2012). It describes a community policing
strategy. If you read this without the context of any first-hand
experience or historical background (e.g., Cointelpro, MK Ultra, and
Stasi), it might seem innocuous. However, if you’re familiar with gang
stalking and its historical predecessors, it takes on a much darker
character.
Operation Weed and Seed
A
strategy within the U.S. Department of Justice’s Office of Justice
Programs that incorporates community-based initiatives. It is an
innovative and comprehensive multi-agency approach to law enforcement,
crime prevention, and community revitalization.
The Weed and Seed Strategy
Operation
Weed and Seed is foremost a strategy–rather than a grant program– which
aims to prevent, control, and reduce violent crime, drug abuse, and
gang activity in targeted high-crime neighborhoods across the country.
Weed and Seed sites range in size from several neighborhood blocks to 15
square miles.
The
strategy involves a two-pronged approach: law enforcement agencies and
prosecutors cooperate in “weeding out” criminals who participate in
violent crime and drug abuse, attempting to prevent their return to the
targeted area; and “seeding” brings human services to the area,
encompassing prevention, intervention, treatment, and neighborhood
revitalization.
A
community-orientated policing component bridges weeding and seeding
strategies. Officers obtain helpful information from area residents for
weeding efforts while they aid residents in obtaining information about
community revitalization and seeding resources.
Note
that this law enforcement model can be exploited not just by government
agencies, but also by private groups and individuals for their own
agendas. I would suggest that is exactly what is happening. Private
organizations and individuals who have the relevant skill sets,
connections to law enforcement and intelligence agencies, and assets to
hire private investigators, can either create illicit “neighborhood
watch” programs to monitor and harass their targets, or they can exploit
existing programs by feeding information (whether true or false) about
their targets to law enforcement personnel to have the victims become
subjects of investigation and surveillance.
The
“Weed and Seed” program is the most explicit official statement of the
institutional philosophy behind gang stalking – namely, that the victims
are deserving of persecution because they are potential criminals,
socially marginal dissidents, drug-users, whistle-blowers,
trouble-makers, etc. Essentially, the targeted individuals are the “weeds” that need to be removed (or at least isolated and suppressed).
__________________________________________________________
14. Disinformation
The Role of Disinformation in Gang Stalking
Gang
stalking is all about deception, so secrecy is a primary element.
Inevitably though, a wide-scale program will involve exposure, so
another major component of gang stalking (and of counterintelligence
operations generally) is disinformation – which is used to mitigate the
effects of public exposure.
The
effectiveness of disinformation derives from the fact that most people –
unlike say, con artists, espionage agents, and detectives – don’t
usually consider that the information they’re encountering might be a
batch of deliberate lies.
As
previously noted, gang stalkers lay the groundwork for the deception by
limiting the harassment tactics to things which will tend to be
dismissed as benign everyday occurrences and coincidences by non-victims
when they are described (neighbors who are noisy and rude, etc.). This
makes it an uphill battle for gang stalking victims to persuade people
about what is being done to them. The problem is compounded by the fact
that sadly, most Americans are totally ignorant of their government’s
non-disputed history of similar programs, such as Cointelpro and MK
Ultra.
Operation Mockingbird
Sadly,
most Americans are thoroughly ignorant of the use of disinformation
campaigns by the U.S. government. This is so notwithstanding a long
history of such tactics.
One
of the most famous programs in which America’s intelligence community
systematically lied to the American public ocurred in the 1950s. Here is
a portion of a Wikipedia entry about it:
Operation Mockingbird was
a secret Central Intelligence Agency campaign to
influence media beginning in the 1950s. Organized by Cord
Meyer and Allen W. Dulles in the 1950s, it was later led by Frank
Wisner after Dulles became head of CIA. The organization recruited
leading American journalists into a network to help present the CIA’s
views, and funded some student and cultural organizations, and magazines
as fronts. As it developed, it also worked to influence foreign media
and political campaigns, in addition to activities by other operating
units of the CIA.
“By the early 1950s, Wisner ‘owned’ respected members of The New York Times, Newsweek, CBS and other communications vehicles.”[3]
The
usual methodology was placing reports developed from intelligence
provided by the CIA to witting or unwitting reporters. Those reports
would then be repeated or cited by the preceding reporters which in turn
would then be cited throughout the media wire services. These networks
were run by people with well-known liberal but pro-American big business
and anti-Soviet views such as William Paley (CBS), Henry
Luce (Time and Life Magazine), Arthur Hays Sulzberger (New York
Times), Alfred Friendly (managing editor of the Washington Post), Jerry
O’Leary(Washington Star), Hal Hendrix (Miami News), Barry Bingham,
Sr. (Louisville Courier-Journal), James Copley (Copley News Services)
and Joseph Harrison (Christian Science Monitor).[7]
The Office
of Policy Coordination (OPC) was funded by siphoning of funds intended
for the Marshall Plan. Some of this money was used to bribe journalists
and publishers.
According
to Alex Constantine (Mockingbird: The Subversion Of The Free Press By
The CIA), in the 1950s, “some 3,000 salaried and contract CIA employees
were eventually engaged in propaganda efforts”. Wisner was able to
constrain newspapers from reporting about certain events, including the
CIA plots to overthrow the governments of Iran (see: Operation Ajax)
and Guatemala(see: Operation PBSUCCESS).[9]
3 – Deborah Davis (1979). Katharine the Great. pp. 137–138.
7 – Carl Bernstein (20 October 1977). “CIA and the Media”. Rolling Stone Magazine.
9 – Alex Constantine (2000). Mockingbird: The Subversion Of The Free Press By The CIA.
Current U.S. Government Policy on Lying
The
values associated with Operation Mockingbird are alive and well in
America’s federal government today – with its penchant for secrecy and
for spying on Americans – and its casual attitude about the Constitution
and honesty.
An article by journalist Glenn Greenwald in January 2010 in Salon.com called
attention to the shockingly Orwellian view of news and propaganda in
both the George W. Bush and Barack Obama administrations. In particular,
Greenwald focused on a member of the Obama administration.
Cass
Sunstein – a close confidant of President Obama – who served as
Administrator of the Office of Information and Regulatory Affairs from
September 2009 to 2012 – has an interesting view on lying by the federal
government: he favors it.
“In
2008, while at Harvard Law School, Sunstein co-wrote a truly pernicious
paper proposing that the U.S. Government employ teams of covert agents
and pseudo-”independent” advocates to “cognitively infiltrate”
online groups and websites — as well as other activist groups — which
advocate views that Sunstein deems “false conspiracy theories” about the
Government. This would be designed to increase citizens’ faith in
government officials and undermine the credibility of conspiracists.
….Sunstein
advocates that the Government’s stealth infiltration should be
accomplished by sending covert agents into “chat rooms, online social
networks, or even real-space groups.” He also proposes that the
Government make secret payments to so-called “independent” credible
voices to bolster the Government’s messaging (on the ground that those
who don’t believe government sources will be more inclined to listen to
those who appear independent
while secretly acting on behalf of the Government). This program
would target those advocating false “conspiracy theories,” which they
define to mean: “an attempt to explain an event or practice by reference
to the machinations of powerful people, who have also managed to
conceal their role.”
Glenn Greenwald’s article:
Cass Sunstein’s Harvard Law School paper:
Slandering Critics of Corporations
For
a fascinating look at the specific ways that disinformation is used by
U.S. government agencies and their corporate contractors, you should
read the article in the Nation which I mentioned previously in this
overview (
“The Strange Case of Barrett Brown” by Peter Ludlow, June 18, 2013).
That
article describes, for example, how a group of private intelligence and
security contractors with close government ties developed an operation
whose objective was to discredit a group which was critical of the
Chamber of Commerce, and to discredit others, such as Glenn Greenwald –
the journalist who later famously revealed the NSA surveillance program
information provided by whistle-blower Edward Snowden in 2013:
Its
main objective was to discredit critics of the Chamber of Commerce,
like Chamber Watch, using such tactics as creating a “false document,
perhaps highlighting periodical financial information,” giving it to a
progressive group opposing the Chamber, and then subsequently exposing
the document as a fake to “prove that US Chamber Watch cannot be trusted
with information and/or tell the truth.” In addition, the group
proposed creating a “fake insider persona” to infiltrate Chamber Watch.
They would “create two fake insider personas, using one as leverage to
discredit the other while confirming the legitimacy of the second.” The
leaked e-mails showed that similar disinformation campaigns were being
planned against WikiLeaks and Glenn Greenwald.
If
operations such as that one were not proven by the documents obtained
by hackers, many people would dismiss the allegations of such activities
as tin-foil hat conspiracy theories.
Another
example (among many) happened in 2012. When a reporter and editor at
USA Today investigated one of the Pentagon contractors being paid to
spread propaganda, that contractor began a secret smear campaign against
them.
“Fake
Twitter and Facebook accounts were created in their names, along with a
Wikipedia entry and dozens of message board postings and blog comments.
Websites were registered in their names…”
A
proxy service was used to hide the identity of the owner of the
websites, and another website was registered to a non-existent address.
Here is an article about it.
Government Front Groups
The
U.S. government adds to the wall of secrecy, deception, and ignorance
which surrounds gang stalking by using four major disinformation
tactics. Each tactic is a variation on the same general strategy –
namely, to discredit gang stalking victims by casting doubts on their
intelligence and sanity.
One
tactic is to create faux support groups for gang stalking victims.
Freedom From Covert Harassment and Surveillance (FFCHS), which I discuss
in detail in its own section of this website, is the main example.
FFCHS was obviously created so that victims will turn to them – rather
than forming their own legitimate advocacy groups to lobby Congress and
the media to investigate gang stalking. As I explain in that section,
everything about the group is designed to convey the impression that
people who claim to be gang stalking victims should not be taken
seriously.
Websites
A
second tactic is the creation of numerous websites about gang stalking
which are filled with stupidity and extraneous information. Again, the
objective is to discredit all self-proclaimed gang stalking victims by
making it appear that they are paranoid tin-foil hat wearing morons.
An
honest intelligent person – even with no personal experience with gang
stalking – would not have trouble distinguishing the relatively credible
websites such as those I cite in the “Recommended Websites” section of
this website from those cited in the recommended sites on the FFCHS
website.
“Sock-Puppets” (Online Personas)
A
third form of disinformation is the use of “sock-puppets” (personas) to
monitor and discredit legitimate websites and social media entities
which discuss gang stalking.
Anyone
who reads the comments posted online whenever the subject of gang
stalking is raised, will note that reports of gang stalking almost
invariably attract sarcastic – but ultimately unconvincing – statements
by forum trolls, registering their skepticism.
One
expects that sort of verbal warfare on Internet forums related to
political issues, but you have to wonder why the relatively obscure
topic of gang stalking attracts such a dedicated army of detractors. As
Hamlet’s mother observed, sometimes people “protest too much.”
As
this article posted on LiveLeak notes,
a former CIA clandestine service trainee and DIA analyst revealed that
the FBI and CIA use trolls to monitor social media and interact with
users to discredit information disseminated on the web.
Most
mainstream news media corporations dutifully avoid discussing the
extent to which the U.S. government and its private intelligence
contractors systematically spread lies online by means of “sock-puppets”
– fake persons.
Thankfully,
some news sources do not view themselves as tools for spreading
propaganda on behalf of corrupt U.S. agencies and corporations.
The Guardian newspaper – which published the famous revelations about NSA surveillance leaked by Edward Snowden –
reported in July 2013 on
the sneaky (and possibly illegal) proposals by a consortium of private
intelligence contracting firms, such as Stratfor, to spread lies on the
Internet on behalf of their corporate clients, using personas:
“[The intelligence firms were] involved
in another scheme to deploy sophisticated software-based fake people
across social networks in order to infiltrate and mislead.”
Faux Articles Planted in the News Media
Finally,
the fourth disinformation tactic is to plant articles in the news media
which create the impression that gang stalking exists only in the minds
of delusional individuals.
The prime example of this – arguably a textbook case of the art of disinformation – is a lengthy
New York Times article on gang stalking called
“Sharing Their Demons on the Web” (November 13, 2008).
Because
of its relevance to material in the “Gang Stalking Documents” section
of this website, the following information also appears there. Please
forgive the redundancy.
FBI
whistle-blower Ted Gunderson (former head of the Los Angeles FBI
office) was a key figure in exposing gang stalking, yet he goes
unmentioned in the Times piece. That should be a giant red warning flag to any reader armed with that information who isn’t retarded.
Even
if the “reporter” had determined that Gunderson’s claims arose from the
fact that he simply became delusional for some reason after a long
high-profile law enforcement career, you would think that finding would
be worth mentioning. Not a word.
That
lengthy article also failed to include any interviews with the licensed
private investigators who have written on the subject of gang stalking,
such as David Lawson and John B. Lopes.
Instead,
the only “experts” interviewed for the article were four mental health
professionals (psychiatrists and psychologists) who discussed mental
illness and delusions. The one other person interviewed was someone who
supposedly claimed to be a victim of gang stalking, Derrick Robinson,
who is identified as a janitor in Cincinnati, and president of FFCHS –
the aforementioned support group for gang stalking victims.
Most readers of the Times article
would not be familiar with FFCHS, and would have no way of knowing – or
even suspecting – that it’s a disinformation front group – as I detail
in the FFCHS section of this website.
Note
that the mental health experts quoted were not asked about their
knowledge of crimes (such as stalking) – let alone their views on the
plausibility of the existence of a modern version of the FBI’s
Cointelpro. In fact, remarkably, the article makes no mention of
Cointelpro whatsoever.
Also
note that the one supposedly self-proclaimed gang stalking victim, Mr.
Robinson, is a janitor – and he is the head of the victims support
group. The intended takeaway is that the most capable member of the
community of self-proclaimed victims of organized stalking – the one
with the wherewithal to become head of their national organization – is a
janitor.
The
reader is left to infer that the rest of the self-proclaimed gang
stalking victim community must really be losers if he’s their brightest
bulb. It simply would not have served the objective of the “reporter” to
discuss gang stalking victims who were professionals, such as the
aforementioned FBI special agent, Mr. Gunderson, or the attorney, Mr.
Labella.
Just
to be sure readers got the message though, a psychiatrist quoted in the
article mentioned that “These people lead quietly desperate lives.”
(Read “losers.”)
A
final point about the article: none of the websites cited are
legitimate, credible websites, such as those I have listed in the
“Recommended Websites” section of this blog. If the Times readers
had been directed to any of the sites which I recommend, they would
have encountered discussions of gang stalking very much at odds with
what they were reading in the Times. The websites mentioned in
the article – such as Gang Stalking World (as distinguished from
Gangstalkingworld.wordpress.com) are badly-edited and filled with
extraneous garbage. Most likely, they are also examples of deliberate
disinformation.
You can read the Times article
at the link below if you want to see a textbook case of disinformation
planted by the government in the mainstream news media – the sort of
thing people like Noam Chomsky get marginalized for warning people
about. (Incidentally, for more on the way government apologists in the
media tend to dismiss people like Chomsky who deviate from political
orthodoxies, see my March 23, 2013 entry in the “Police State Amerika
News” section of this website.)
If,
despite the historical background of Cointelpro, and despite all the
other information provided in this website, you conclude that this
article is simply an example of journalistic incompetence at the
nation’s “Paper of Record,” then I have a bridge to sell you.
Incidentally, by a remarkable coincidence, an article that was virtually identical to the Times piece was published by ABC News one month later (although it makes no reference to the Times piece
that preceded it). By remarkable coincidence, the “reporter” at ABC
interviewed the same psychiatrist who was interviewed by the Times,
Ken Duckworth. Also by remarkable coincidence, the “reporters” in both
cases were third-tier shills no one has heard of – rather than, say,
Pulitzer Prize-winning investigative journalists.
Also
by coincidence, the ABC article – like the Times article – failed to
include any reference to the important high-profile credible
whistle-blower key witness who supports the claims of gang stalking
victims, Ted Gunderson. The ABC News article which involved such an
extraordinary number of coincidences also failed to even mention
Cointelpro or MK Ultra – or any other actual relevant non-disputed
government conspiracies, and focused exclusively on discussions of
delusional thinking. If you want to read this ground-breaking,
hard-hitting piece of brave investigative journalism by the intrepid
Lauren Cox,
here is the link.
There
is a down-side for gang stalkers to all these efforts at
disinformation: they constitute evidence of a conspiracy when viewed in
the context of other information – such as I have provided in this
website.
A final observation about the two articles cited above:
It’s
interesting that those two rare examples of mainstream news media
articles about organized stalking both appeared (about the same time)
years ago, and then the subject has been off the radar since then.
Since
that time, the number of online accounts of gang stalking – such as
this website – have only increased, and the number of published articles
in the alternative media alleging a re-emergence of Cointelpro (such as
those cited in section 4 of this overview) have increased. Yet the New
York Times and ABC have not re-visited the issue.
That
makes perfect sense as a disinformation strategy. Anyone searching for
mainstream news reports on gang stalking will see that – apparently – a
couple of major news outlets looked into the phenomenon years ago and
found it was all rubbish. Case closed. Further articles – even if they
were similarly dismissive – might callattention to the topic in an unhelpful way.
__________________________________________________________
15. The Wall of Silence Which Surrounds Gang Stalking
“The first rule of fight club is you do not talk about fight club.”– from the 1999 film Fight Club
Sometimes
people violate the rule and they do mention fight club. In the
following case, both the news media and a police lieutenant violated
the rule and explicitly mentioned gang stalking in a TV news report.
A
local TV news broadcast in California on January 29, 2011 (on KION –
Channel 46 and KCBA – Channel 35) featured a report about gang stalking
in which the reporters used the term and so did Lieutenant Larry Richard
of the Santa Cruz Police Department. (This link is also included in the
“Published Articles” section of this overview.)
Instances
like the one above are the exception though. Despite its apparent
pervasiveness, gang stalking is rarely discussed publicly by the
mainstream media – let alone by government officials.
What
mainly accounts for that silence is the secrecy and disinformation of
the perpetrators, and the use of tactics chosen for their lack of
incriminating evidence.
Another
factor, presumably, is that those members of the media and civil rights
groups who are aware of the crime do not wish to risk being publicly
associated with any claims likely to be perceived by casual observers as
a paranoid conspiracy theory.
FBI’s silence on gang stalking
America’s
agency with primary responsibility for domestic counterintelligence
operations, the FBI, is notoriously secretive about its activities. One
way that silence is maintained is by the agency’s exemption from the
Whistleblower Protection Act. Anyone wishing to expose misconduct at the
FBI could face severe legal repercussions.
Probably
the main reason Americans are mostly unaware of the prevalence of
organized stalking is that there has not been a major exposure by an FBI
whistle-blower. Nothing comparable to the revelations by Edward Snowden
about the NSA’s domestic spying has occurred at the FBI.
“…count on one thing: we undoubtedly don’t yet know the worst or most illegal aspects of this era of “intelligence.” After
all, while Snowden “liberated” up to 1.7 million National Security
Agency documents (many of them not yet looked at, analyzed, or written
about), there have been no similar twenty-first-century break-ins at the
FBI, the CIA, or other parts of the American intelligence community (or
for that matter at the Pentagon and the Department of Homeland
Security). Massive and shocking as the NSA revelations have been, the curtain has only been pulled back on a corner of
the new Washington world that we, the people, continue to fund, even if
we aren’t considered important enough to know anything about it.”
[emphasis added]
ACLU’s silence on gang stalking
While
it would be understandable for a group like the ACLU to be circumspect
for such reasons, the more one learns about organized stalking, the more
one realizes how unlikely it is that people in such organizations are
unaware of what is happening.
Folks
at the ACLU are presumably very familiar with Cointelpro, since it was
part of the history of persecution of civil rights leaders and other
dissidents. It seems inconceivable that the ACLU is unaware of the
allegations that a similar program now exists.
The
ACLU receives well-deserved credit for its willingness to represent
politically-unpopular positions in court. Still, legal advocacy for a
minority cause is a very different thing than challenging a shadowy
extra-judicial program whose essential function is to destroy the lives
of targeted individuals. Ted Gunderson, the former FBI official who
tried – with some success – to expose organized stalking, claimed that
his efforts resulted in him becoming a target himself. Members of the
ACLU have professional careers and families to consider.
It
should be noted that the ACLU has never made any public declarations
that organized stalking is not real. Apparently it’s simpler to just
avoid the topic completely, and not have to worry about being portrayed
as a shill for a conspiracy once it eventually becomes widely exposed. A
similar dynamic might be at work in the news media.
Anyone
who attempts to contact groups such as the ACLU to inquire about their
position on the subject of gang stalking will find that they don’t
respond with skepticism; they just don’t respond at all.
As
I mention in the “Tactics” page of this website, anyone wishing to gain
the attention of the ACLU on the subject of organized stalking should
probably meet face-to-face with members of their local ACLU chapter
rather than trying to contact the organization’s national office.
Censorship (and self-censorship) of the American news media
To
discourage reporting on issues it would rather not see publicly
discussed, the U.S. government has aimed two weapons of intimidation at
the American news media in recent years: surveillance of communication
and prosecution of whistle-blowers.
Following
the AP phone records incident, journalists reported that trusted
sources were becoming noticably more reluctant to provide information.
AP President Gary Pruitt said that sources now “fear that they will be monitored by the government.”
A survey published in November 2013 by
PEN American Center – an association of American writers dedicated to
protecting free expression – found that many published writers in the
U.S. reported that they self-censor on subjects such as military
affairs, mass incarceration, drug policies, the Occupy Wall Street
movement, and criticism of the U.S. government.
The
survey found that 40 percent of the writers polled had either curtailed
their social media activities or seriously considered doing so. In
addition, 33 percent reported deliberately avoiding certain topics – or
at least seriously considered avoiding certain topics – in phone or
email conversations. The survey also revealed that 28 percent had refrained – or seriously considered refraining – “from conducting Internet searches or visiting websites on topics that may be considered controversial or suspicious.”
Doing
its best to chill criticism of the federal government, the Obama
administration has prosecuted more whistle-blowers than all former
presidents combined. The Committee to Protect Journalists published
one of the best articles on this disturbing trend in October 2013 by a former editor of the Washington Post. Some excerpts:
“Six
government employees, plus two contractors including Edward Snowden,
have been subjects of felony criminal prosecutions since 2009 under the
1917 Espionage Act, accused of leaking classified information to the
press—compared with a total of three such prosecutions in all previous
U.S. administrations. Still more criminal investigations into leaks are
under way.”
“Exposing “waste, fraud and abuse” is considered to be whistle-blowing. But exposing
questionable government policies and actions, even if they could be
illegal or unconstitutional, is often considered to be leaking that must
be stopped and punished. This greatly reduces the potential for the press to help hold the government accountable to citizens.”
Alternative media outlets
Some
media programs and websites routinely discuss controversial and
esoteric subjects that reside in the grey area of speculation and rumor –
for example, the Coast-to-Coast am radio show, and websites such as InfoWars.com, and Snopes.com.
Gang
stalking, however, goes conspicuously unmentioned at such places. Try
contacting Snopes to ask whether gang stalking is real; they won’t
answer – let alone explore the topic on their website. When I last
checked the Coast-to-Coast website, the search function yielded
numerous results for “Big Foot,” but zero results for Cointelpro or gang
stalking. In my experience, they also don’t respond to email inquiries
about the topic.
Further reading on self-censorhip and corporate censorhip
Anyone wishing to learn more about the media silence on various “off-limits” topics might want to read Noam Chomsky’s classic,
Manufacturing Consent (or watch the documentary by that name on YouTube) and Kristina Borjesson’s
Into the Buzzsaw.
_____________________________________________________
16. Shining a Light on the Cockroaches
Gang
stalking is conducted in secret because, like its predecessors
Cointelpro and MK Ultra, it is illegal and unconstitutional. Stalking –
described as such, or as “criminal harassment” or “criminal menace” – is
now a crime under the laws of every state in America.
The
first state to criminalize stalking was California, in 1990. Within
three years, all states had done so. Stalking is illegal because the
vast majority of Americans deem it morally reprehensible and an assault
on the basic rights and freedoms of the victims.
Gang
stalkers know that most people – if they fully understood what gang
stalkers were engaged in – would regard them as the human equivalent of
cockroaches, so they skulk around and ply their trade in the shadows.
They
don’t have to worry about being caught and prosecuted however, because
(a) their tactics are inherently difficult to prove legally as discussed
above, and (b) their crimes are supported directly and indirectly by
people with power and money and government connections.
Even
if you assume that some/most/all individuals targeted for gang stalking
are in some way “undesirable” and deserving of persecution, you should
note that gang stalking is very different from “shaming.” The historical
practice of a communities shaming individuals had the imprimatur of the
society. If gang stalkers had such a sanction, they wouldn’t have to
conduct their activities in secret.
Instead,
gang stalking is largely a game played by people who are wealthy and/or
well-connected to the police state infrastructure. For their personal
vendettas and agendas, they exclusively wield gang stalking as a weapon
that is unavailable to most people.
Exposing
what is happening is the challenge for victims of gang stalking – or
anyone who believes that America should be a constitutional free nation
instead of a quasi-police state run by plutocrats and neo-fascist law
enforcement and intelligence agents with the help of their various
minions, opportunistic parasites, and useful idiots.
The
balance of power is completely tipped in favor of the bad guys in the
battle between gang stalkers and targeted individuals. Also, cowardice
and careerism by politicians and members of the mainstream press make it
unlikely that much help will spontaneously emerge from those quarters.
On
the other hand, civilian activists successfully exposed the Cointelpro
conspiracy, which helped lead to the Senate Church Committee
investigations, so there is precedent for eventual victory by the good
guys. Mind you, those activists had to break into an FBI office to get
the documents which led to that exposure, so a certain amount of courage
is required.
A
final point: the Internet is a game-changer; it has the potential to
expose gang stalking, which will ultimately lead to the program’s
demise. As I noted in my essay “Gang Stalking and America’s Police State
Government” elsewhere in this website, the digital public square is
already filled with information and rhetoric which the government would
prefer to censor but cannot, posted by Americans fed-up with the secrecy
and abuses of power in the upper echelons of government and
corporations.
Please help spread the word.
__________________________________________________________
If
you can expose the criminal participation in gang stalking by private
intelligence/security firms, lawless federal agencies, and local
“community policing” vigilante groups, please do so. America needs more
patriots like Edward Snowden, Jeremy Hammond, Barrett Brown, Daniel
Ellsberg, and Frank Serpico.
__________________________________________________________
FightGangStalking.comG









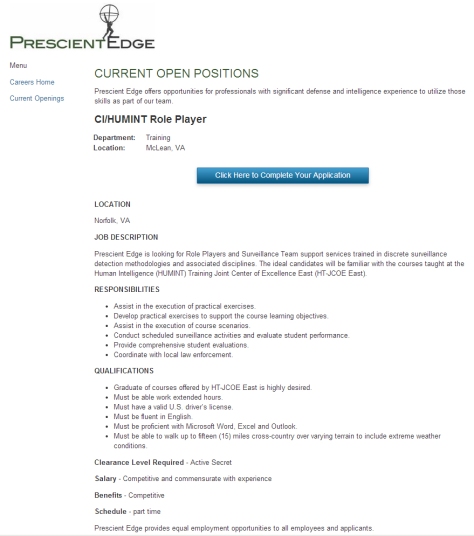






















No comments:
Post a Comment